All new Dell laptops and desktops shipped since August 2015 contain a serious security vulnerability that exposes users to online eavesdropping and malware attacks. Dell says it is prepping a fix for the issue, but experts say the threat may ultimately need to be stomped out by the major Web browser makers.
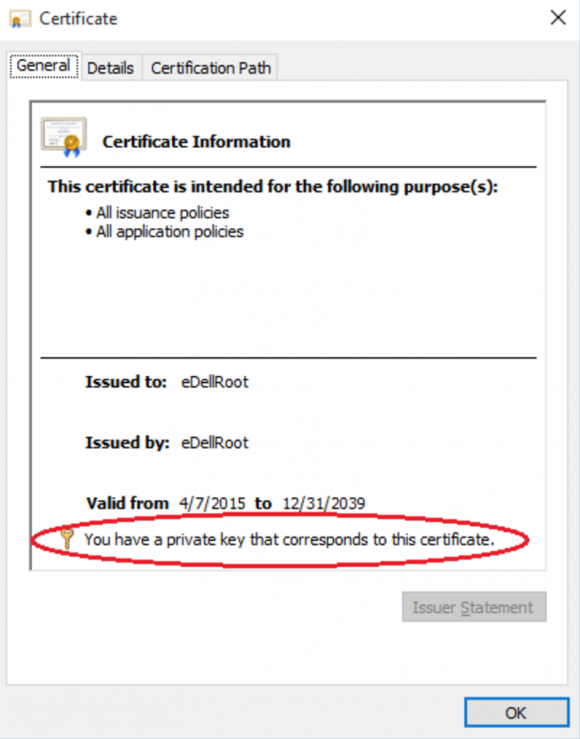
 At issue is a root certificate installed on newer Dell computers that also includes the private cryptographic key for that certificate. Clever attackers can use this key from Dell to sign phony browser security certificates for any HTTPS-protected site.
At issue is a root certificate installed on newer Dell computers that also includes the private cryptographic key for that certificate. Clever attackers can use this key from Dell to sign phony browser security certificates for any HTTPS-protected site.
Translation: A malicious hacker could exploit this flaw on open, public networks (think WiFi hotspots, coffee shops, airports) to impersonate any Web site to a Dell user, and to quietly intercept, read and modify all of a vulnerable Dell system’s Web traffic.
According to Joe Nord, the computer security researcher credited with discovering the problem, said the trouble stems from a certificate Dell installed named “eDellRoot.”
Dell says the eDellRoot certificate was installed on all new desktop and laptops shipped from August 2015 to the present day. According to the company, the certificate was intended to make it easier for Dell customer support to assist customers in troubleshooting technical issues with their computers.
“We began loading the current version on our consumer and commercial devices in August to make servicing PC issues faster and easier for customers,” Dell spokesperson David Frink said. “When a PC engages with Dell online support, the certificate provides the system service tag allowing Dell online support to immediately identify the PC model, drivers, OS, hard drive, etc. making it easier and faster to service.”
“Unfortunately, the certificate introduced an unintended security vulnerability,” the company said in a written statement. “To address this, we are providing our customers with instructions to permanently remove the certificate from their systems via direct email, on our support site and Technical Support.”
In the meantime, Dell says it is removing the certificate from all Dell systems going forward.
“Note, commercial customers who image their own systems will not be affected by this issue,” the company’s statement concluded. “Dell does not pre-install any adware or malware. The certificate will not reinstall itself once it is properly removed using the recommended Dell process.”
It’s unclear why nobody at Dell saw this as a potential problem, especially since Dell’s competitor Lenovo suffered a very similar security nightmare earlier this year when it shipped an online ad tracking component called Superfish with all new computers.
Researchers later discovered that Superfish exposed users to having their Web traffic intercepted by anyone else who happened to be on that user’s local network. Lenovo later issued a fix and said it would no longer ship computers with the vulnerable component.
Dell’s Frink said the company would not divulge how many computers it has shipped in the vulnerable state. But according to industry watcher IDC, the third-largest computer maker will ship a little more than 10 million computers worldwide in the third quarter of 2015.
Zakir Durumeric, a Ph.D. student and research fellow in computer science and engineering at the University of Michigan, helped build a tool on his site — https://zmap.io/dell — which should tell Dell users if they’re running a vulnerable system.
Durumeric said the major browser makers will most likely address this flaw in future updates soon.
“My guess is this has to be addressed by the browser makers, and that we’ll seem them blocking” the eDellRoot certificate. “My advice to end users is to make sure their browsers are up-to-date.”
Further reading:
An in-depth discussion of this issue on Reddit.
Dan Goodin‘s coverage over at Ars Technica.
Update, 1:15 a.m. ET: Added link to Dell’s instructions for removing the problem.
Source: Krebs