Cybercrime takes many forms, but one of the more insidious and perhaps less obvious manifestations is warranty fraud. This scheme involves con artists who assume the identity of a consumer, complain that a given product has ceased to operate as expected, and demand that the retailer replace the article in question. Such claims turn into a loss for targeted merchants when the scammer hacks an unwitting customer’s account and replaces the customer’s email address with his own address and demands that the retailer ship him a brand new device.
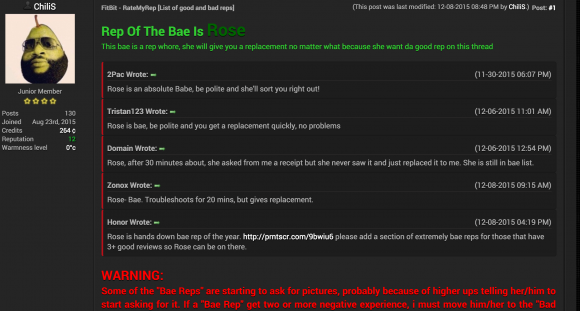
Leakforums is a big source of account takeover and waranty fraud for a variety of products.
Fitness tracking giant Fitbit recently found itself the target of such fraud in the last few months of 2015, when the company noticed large caches of data from customer accounts being posted to Pastebin. To the untrained eye, such data might seem at first glance to indicate that Fitbit had experienced a breach that exposed their user account data. Included in the data dumps posted to Pastebin were details about the make and model number of each user’s fitness tracker, as well as information about the last time the user had synced the device.
But a more nuanced look at the information posted to Pastebin and other public data dump sites indicates that Fitbit is just the latest victim of customer account takeovers powered by breaches at other e-commerce providers.

Hacked Fitbit user accounts sell for about $2 apiece.
I reached out to Fitbit about this and the company’s security chief Marc Bown said the data appears to coming from a couple of sources: Customer computers that have been compromised by password-stealing malware, and customers who re-use the same credentials across a broad swath of sites online.
“They’re mainly interested in the premium devices,” Bown said, referring to the most expensive devices that Fitbit sells — such as the Surge, which retails for about $250. “Those are the ones that we’re seeing are most targeted for warranty fraud.”
Bown said the fraudsters will log in to the customer’s account and change the email address on the customer’s account. The scammers then call Fitbit’s customer service folks, claim that their device has stopped working, and demand a replacement.
“Basically, they start a support case with customer service, but before they do that, they change the email address on the account they hacked to an address that they control, and at that point they are the customer,” Bown said. “For a lot of customers, this ends up creating a pretty negative experience.”
Bown said after several weeks of battling warranty fraud, the company has more or less solved the problem by educating their customer service employees and assigning risk scores to all warranty replacement requests.
“Account takeover is a thing for all online organizations,” Bown said. “If we see an account that was used in a suspicious way, or a large number of login requests for accounts coming from a small group of Internet addresses, we’ll lock the account and have the customer reconfirm specific information.”
E-commerce companies can increase the level of security for user accounts by requiring two-step or two-factor authentication, which usually involves sending a one-time code to the user’s mobile device that needs to be inputted in addition to the customer’s username and password. Bown said Fitbit is considering adding this capability to user accounts.
“I’m not sure the type of user who is using the same password at every site is the great target for that,” Bown said. “But we should offer it, and it’s something we plan to offer in 2016 natively.”
Source: Krebs