Staminus Communications Inc., a California-based Internet hosting provider that specializes in protecting customers from massive “distributed denial of service” (DDoS) attacks aimed at knocking sites offline, has itself apparently been massively hacked. Staminus’s entire network was down for more than 20 hours until Thursday evening, leaving customers to vent their rage on the company’s Facebook and Twitter pages. In the midst of the outage, someone posted online download links for what appear to be Staminus’s customer credentials, support tickets, credit card numbers and other sensitive data.
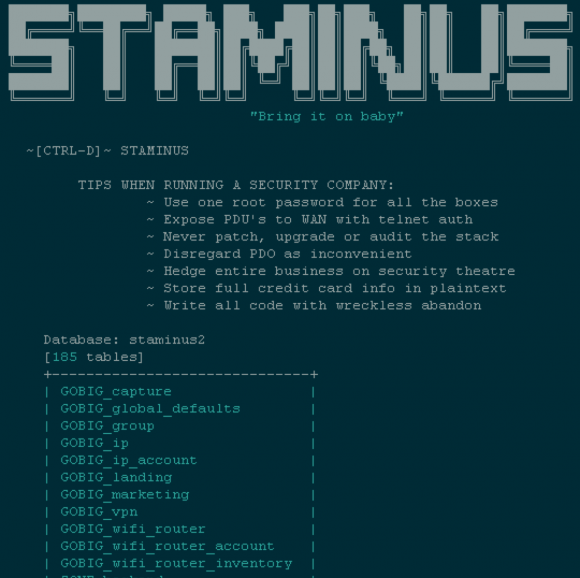
The e-zine posted online Thursday following an outage at Staminus Communications.
Newport Beach, Calif.-based Staminus first acknowledged an issue on its social media pages because the company’s Web site was unavailable much of Thursday.
“Around 5am PST today, a rare event cascaded across multiple routers in a system wide event, making our backbone unavailable,” Staminus wrote to its customers. “Our technicians quickly began working to identify the problem. We understand and share your frustration. We currently have all hands on deck working to restore service but have no ETA for full recovery.”
Staminus now says its global services are back online, and that ancillary services are being brought back online. However, the company’s Web site still displays a black page with a short message directing customers to Staminus’s social media pages.
Meanwhile, a huge trove of data appeared online Thursday, in a classic “hacker e-zine” format entitled, “Fuck ’em all.” The page includes links to download databases reportedly stolen from Staminus and from Intreppid, another Staminus project that targets customers looking for protection against large DDoS attacks.
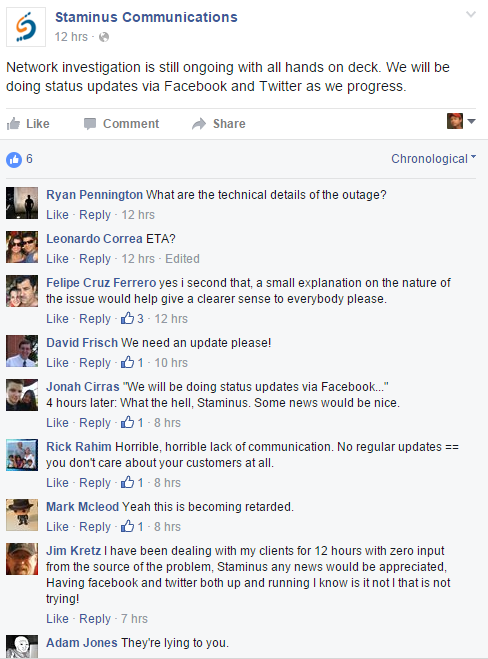
Frustrated Staminus customers vent on the company’s Facebook page.
The authors of this particular e-zine indicated that they seized control over most or all of Staminus’s Internet routers and reset the devices to their factory settings. They also accuse Staminus of “using one root password for all the boxes,” and of storing customer credit card data in plain text, which is violation of payment card industry standards.
Staminus so far has not offered any additional details about what may have caused the outage, nor has it acknowledged any kind of intrusion. Several Twitter accounts associated with people who claim to be Staminus customers frustrated by the outage say they have confirmed seeing their own account credentials in the trove of data dumped online.
I’ve sent multiple requests for comment to Staminus, which is no doubt busy with more pressing matters at the moment. I’ll update this post in the event I hear back from them.
It is not unusual for attackers to target Anti-DDoS providers. After all, they typically host many customers whose content or message might be offensive — even hateful — speech to many. For example, among the company’s many other clients is kkk-dot-com, the official home page of the Ku Klux Klan (KKK) white supremacist group. In addition, Staminus appears to be hosting a large number of internet relay chat (IRC) networks, text-based communities that are often the staging grounds for large-scale DDoS attack services.
Source: Krebs