We are always talking about ransomware and the importance of keeping your corporate network protected, and we want to warn our readers about the popular Trojan attacks that are going after small and medium sized businesses. But how do you know when it’s a Trojan? How can you secure yourself against Trojans?
5 Things You Should Know
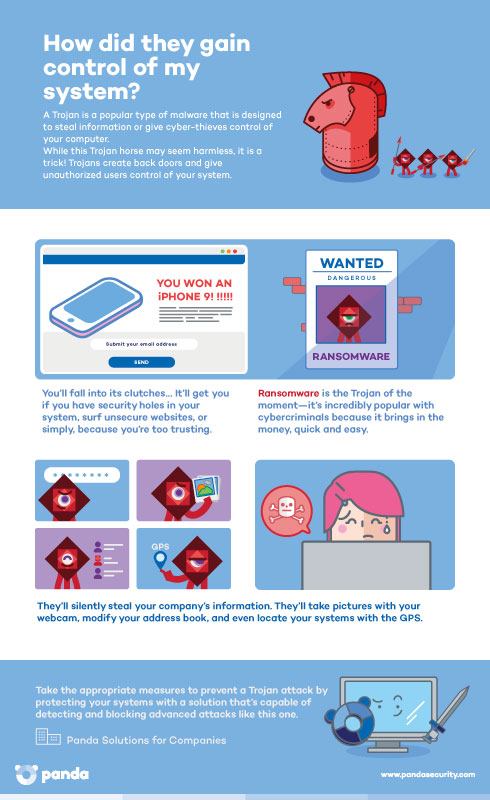
- They are malicious software programs designed to rob information or take control of the computer. These attacks target businesses that manage top-secret information.
- Trojans are the most popular type of malware and have been for years. Running closely behind them is Ransomware.
- Trojans seem harmless but as soon as they are executed they will damage systems and steal information.
- Most of them create backdoors and give unauthorized users remote access and control over your system…but they go unnoticed!
- Trojan horse: The professional trickster. It disguises itself as something its not.
 Trojans: Topping the Charts
Trojans: Topping the Charts
Trojans make up the majority of the 227,000 malware samples that are detected daily by PandaLabs. Month after month, they continue to be in first place as the most created malware.
Increasing since the second quarter of 2016, Trojans currently make up 66.81% of the new malware samples created this quarter. Viruses make up 15.98% (Worms 11.01%, PUPs 4.22% and Adware/Spyware at 1.98%).
What do their creators want to achieve?
- Steal personal and corporate information: bank information, passwords, security codes, etc.
- Take photos with webcams, if there are any!
- Erase the hard-drive.
- Capture incoming and outgoing text messages.
- Seize the call registry.
- Access (consult, eliminate and modify) the address book.
- Make calls and send SMS messages.
- Use the GPS to figure out the geographic location of the device.
How can we protect ourselves from Trojans?
– Avoid downloading content from unfamiliar websites or sites with dubious reputations.
– Monitor downloads from p2p applications.
– Keep your advanced security solution updated. Install one of the Panda Solutions for Companies that best adapts to you and protect yourself from these dangers.
– Analyze your computer for free and make sure it’s Trojan free.
The post They can remotely access and control my computer? appeared first on Panda Security Mediacenter.
Source: Panda

