Hzone threatened to infect the admin for a site that planned to write about its week-long spillage of a laundry list’s worth of PII. Source: Sophos
Sources at multiple financial institutions say they are tracking a pattern of fraud indicating that thieves have somehow compromised the credit card terminals at checkout lanes within multiple Safeway stores in California and Colorado. Safeway confirmed it is investigating skimming incidents at several stores. Banking sources say they’ve been trying to figure out why so many […]
Just like we saw in 2014, it has been a year full of scams, tricks, and swindles aimed at WhatsApp, the ever popular messaging service. We don’t doubt for a moment that 2016 will be any different, so we’d like to remind you of how cybercriminals look for their potential victims by taking a look […]
Download PDF version Download EPUB Download Full Report PDF Download Full Report EPUB Top security stories Evolution of cyber threats in the corporate sector Overall statistics for 2015 Predictions 2016 The year in figures In 2015, there were 1,966,324 registered notifications about attempted malware infections that aimed to steal money via online access to bank accounts. Ransomware programs […]
The makers of MacKeeper — a much-maligned software utility many consider to be little more than scareware that targets Mac users — have acknowledged a breach that exposed the usernames, passwords and other information on more than 13 million customers and, er…users. Perhaps more interestingly, the guy who found and reported the breach doesn’t even […]
With little more than a month to go before the start of the 2016 tax filing season, the IRS and the states are hunkering down for an expected slugfest with identity thieves who make a living requesting fraudulent tax refunds on behalf of victims. Here’s what you need to know going into January to protect […]
Christmas is around the corner and with it comes the usual round of parties and celebrations. This means that our spare time is taken up more than usual, which has an effect on how we complete our gift shopping. The easiest way around this for most is to take to the Internet, avoiding the queues […]
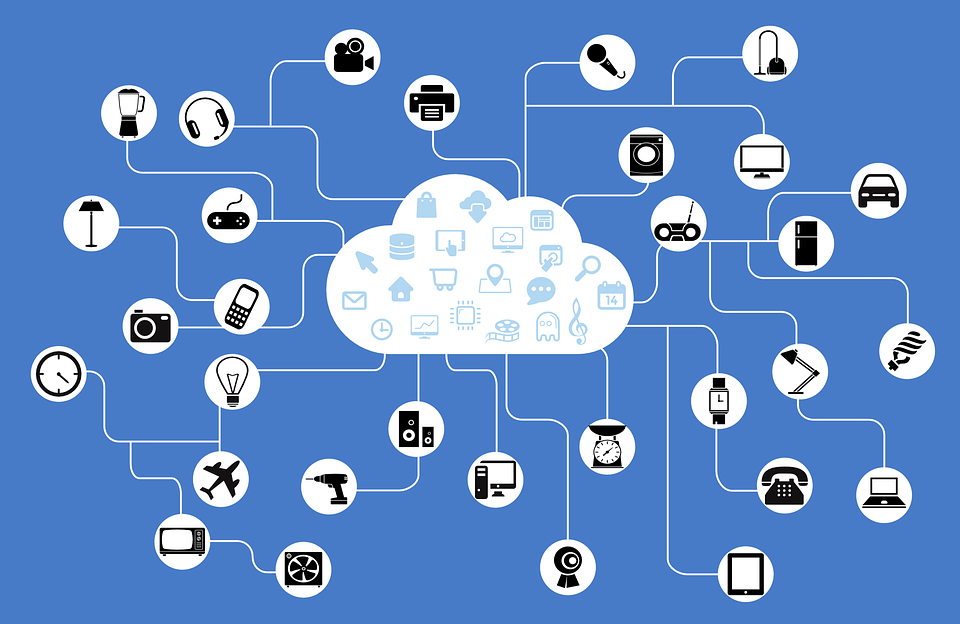
The Internet of Things (IoT) has arrived and it’s here to stay. What might seem a tool that is only used by a select few will soon become a worldwide trend – the lock on your home, your household objects, and even your toothbrush will soon be connected to the network and under control via […]