All new Dell laptops and desktops shipped since August 2015 contain a serious security vulnerability that exposes users to online eavesdropping and malware attacks. Dell says it is prepping a fix for the issue, but experts say the threat may ultimately need to be stomped out by the major Web browser makers. At issue is […]
Amazon has added multi-factor authentication to help customers better secure their accounts from hackers. With this new feature enabled, thieves would have to know your username, password, and have access to your mobile device or impersonate you to your mobile provider in order to hijack your Amazon account. The security feature allows users to receive a one-time code […]
“Has the computer become a black box, even to experienced electrical engineers? Will we be forever reliant upon large, opaque organizations to build them for us? Absolutely not, we say. And to prove our point, we built our very own laptop, from the circuit boards on up.” With this statement the creators of Novena have […]
From NBC News come revelations that ISIS has its very own web-savvy, 24-hour Jihadi Help Desk manned by a half-dozen senior operatives to assist foot soldiers in spreading their message far and wide. My first reaction to this story was disbelief, then envy (hey, where the heck is my 24/7 support?). But soon enough I forgot about all […]
Starwood Hotels & Resorts Worldwide today warned that malware designed to help cyber thieves steal credit and debit card data was found on point-of-sale cash registers at some of the company’s hotels in North America. The disclosure makes Starwood just the latest in a recent string of hotel chains to acknowledge credit card breach investigations, and comes days after […]
Today is Universal Children’s Day, a day set aside for everyone to protect and defend the rights of children. But do we know how to protect children from the dangers involving the Internet and new technologies? It’s important to defend their rights and their innocence in the online world. The internet is a world known […]
A bill introduced in the U.S. House of Representatives on Wednesday targets “swatting,” an increasingly common and costly hoax in which perpetrators spoof a communication to authorities about a hostage situation or other violent crime in progress in the hopes of tricking police into responding at a particular address with deadly force. The Interstate Swatting Hoax […]
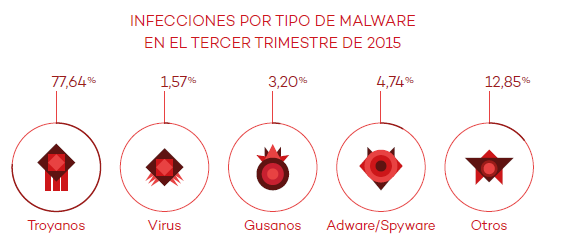
PandaLabs, the laboratory of Panda Security, warns in this, its latest quarterly report, that there has been a wave of cyberattacks where the security and information of various governments has been compromised. A so-called cyberwar between countries has been present in the last few years, however, PandaLabs has detected a growing interest between countries in […]
Download PDF version Introduction The Russian-language cybercrime market is known all over the world. By ‘Russian-language market’ we mean cybercriminals who are citizens of the Russian Federation and some former USSR countries, predominantly Ukraine and the Baltic states. Why is this market known worldwide? There are two main factors: the first of these is frequent […]