Virtualized environments are exceptionally flexible, manageable, fault-tolerant and cost-effective. However, a number of difficulties have to be overcome to protect them from external threats. If this is not done successfully, problems will inevitably arise. This is true of individual virtual machines, as well as the data center as a whole. Unfortunately, malware infections are a […]
A secure system – especially a system that is used to provide security – has to be trusted. But what underpins that trust? What proof do we have that the main components of our trusted system are implemented properly and won’t fail at a critical moment? We mentioned this point in our last article about […]
Thanks to the advent of smartphones, we no longer have to worry about going over our message limit, or sending the same message to different people. Nowadays there is a large selection of different messaging apps to choose from, which allow you to send as many messages to as many people as you like, including […]
The early detection of cyber threats has long been one of the biggest goals for the IT security sector. The rapid evolution of the different types of cyber-attacks has rendered the traditional detection systems helpless to differentiate between, and detect, attack such as advanced persistent threats (APT), which are digital attacks directed at certain systems […]
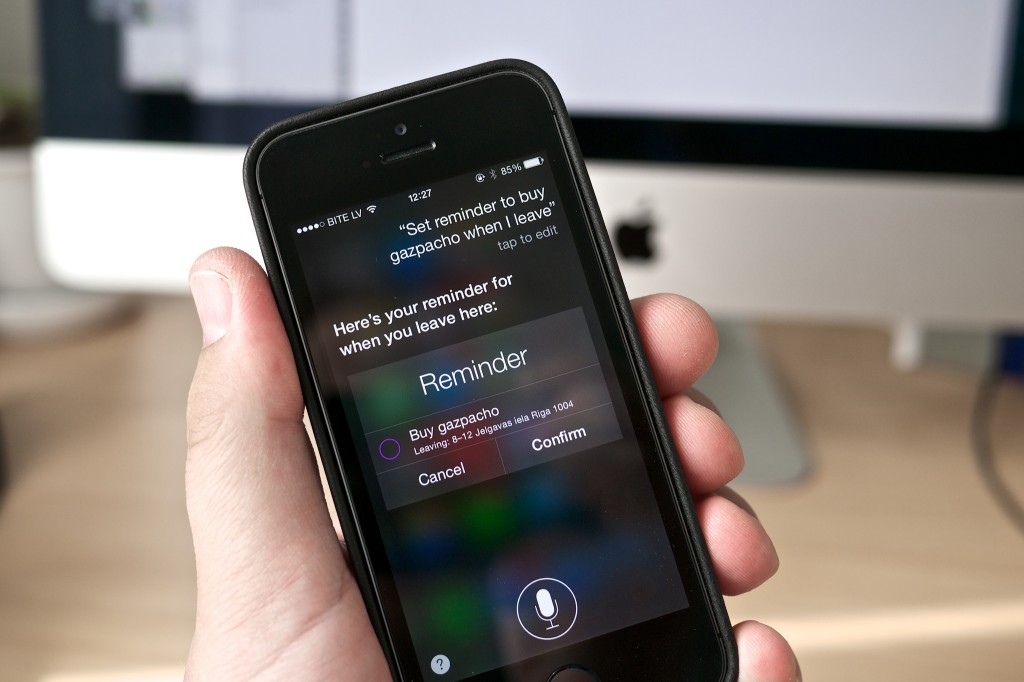
Virtual voice assistants such as Siri and Google Now detect key words when you ask them questions so as to understand and be able to offer you the service that you require. They also have access to the majority of tools built into your phone. For example, Siri is able to search your contact list […]
Scare stories around the Internet of Things (IoT) conjure up images of bad guys in hoodies, who live for hacking and to make the lives of other people harder, inventing millions of ways to infiltrate your life through your gadgets. But is this perception a good enough reason to stop using smart devices? We don’t […]
Download PDF version Q3 events Of all the Q3 2015 events in the world of DDoS attacks and the tools used to launch them, we picked out those that, in our opinion, best illustrate the main trends behind the evolution of these threats. DDoS attacks targeting financial organizations for the purpose of extortion; new techniques […]