Drones have conquered the world: they are used to hunt down tax evaders and illegal hunters, help suppress wildfires, find victims after natural disasters… They even serve as flying cameras to assist in filming movies and for aerial photography. Online retail giant Amazon, for example, is planning on using drones for commercial delivery in order […]
5 tips to maintain your cell phone battery without compromising experience When cell phones appeared on the market they were meant to be used for talk and text. However, things have changed and cellular operators no longer stress about the amount of minutes or texts you are using, but for the amount of data you […]
Wi-Fi networking is absolutely essential to the modern home. From smartphones to games consoles to intelligent thermostats like Nest, virtually every appliance now requires a wireless internet connection. As a result, there is all kinds of valuable information being transmitted across your Wi-Fi network – credit card numbers, passwords and sensitive photos and files. Which […]
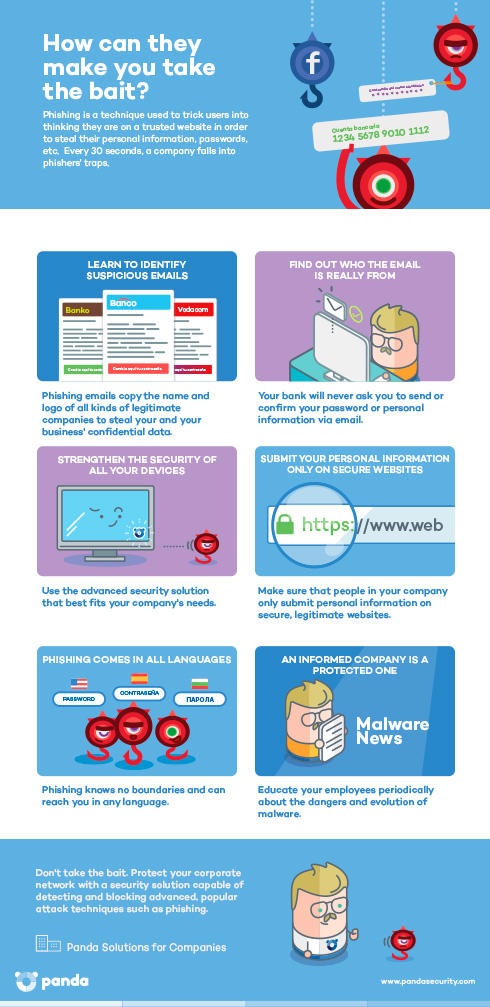
Phishing continues to blight the Internet and is a thorn in the side of companies around the globe. Not only is it one of the most serious problems facing any company with even a minimal activity on the Web, it is also an ever-increasing threat. So much so, that a recent study has revealed that […]
Tips to protect your personal data on online music streaming platforms like Spotify Malvertising – yet another offspring of the online advertising, has been around since 2008. However, in 2016 we’ve been observing more and more creative ways of hackers trying to compromise your system by injecting malicious or malware-laden advertisements. They are getting so […]
That hard disks, pen drives and other physical storage devices are an attractive target for cyber-criminals wanting to steal confidential information from enterprises is something that company managers are well aware of. And, in fact, they try to educate their employees about the need to use those tools properly. However, the now-popular digital cloud, used […]
Something as apparently inoffensive as employees keeping up with the lives of ‘celebs’ on the Internet could be far more dangerous than you think for your company’s IT systems. Whether you like it or not, some employees take advantage of dead time (and not-so-dead time) to look for all the latest gossip and news on […]
Warning – the following article may contain spoilers What it’s true of Black Mirror? Charlton Brooker’s Black Mirror television series has become something of a phenomenon thanks to its almost prophetic predictions about society and technology. Set in the very near future, Black Mirror borrows technology stories from the media, and imagines the worst possible […]
With the arrival of Apple Pay and Samsung Pay in Russia, many are wondering just how secure these payment systems are, and how popular they are likely to become. A number of experts have commented on this, basing their opinions on the common stereotypes of Android being insecure and the attacks which currently take place […]