Though we often speak of electronic waste and the darker side of technology, whose insatiable energy consumption is causing serious harm to the environment, we can actually use technology for good. It’s possible for the internet and our Smartphones to be environmentally friendly. This Sunday, June 5th, we celebrate World Environment Day. We wanted to take […]
For years cybercriminals have had their focus on money, and most specifically in the financial system. For more than a decade they have been mainly targeting the weakest link in the chain: the final user that uses online banking services. This approach has some benefits for these cybercriminals: poor security in the end user, small […]
Workers are the first and the weakest link in the security chain (including your boss), especially if they have not received adequate training to defend themselves against cyber-attackers. Sadly, if malware were to sieve into an employee’s Smartphone or mobile device it could potentially cost a company more than 8,000 euros. This is the beginning […]
Smart watches and fitness bracelets are joining millions of people on the mission to be healthier and more active. These devices are becoming part of our daily lives, and expanding the functions that we already use on our Smartphones. According to the consulting firm IDC, in the first quarter of 2016, wearable technology sales have already increased, mostly due to the smart […]
Children use the Internet for schoolwork, socializing, watching films and cartoons, playing games and much more. But, as we all know, browsing the web can be an unsafe business. In order to control their children’s online activity many parents use specialized software – so-called parental control. This software is usually capable of controlling the amount […]
It was the last weekend of May and just like every year, hackers, forensic experts and pentesters met at the Universal Hall in Berlin for the BerlinSides conference. ‘A con from hacker for hacker’. This years motto is ‘electrifying’ and the badges and shirts show the picture of Nikola Tesla. BerlinSides is the successor of […]
One of the best things about Android’s operating system is the variety of options available with dozens of manufacturers from all backgrounds, hundreds of models on the market, prices for all budgets and features for all tastes. However, the same breadth and depth of product and service offerings which makes Android attractive is, at the same time, one of their […]
We’re sure your browser has been hijacked before. Say you decide to download a program you need from a seemingly reliable website (like Softonic), and you click “install” to begin downloading without really thinking about it. When it finishes downloading, you go back to the browser and you realize that one or more toolbars have […]
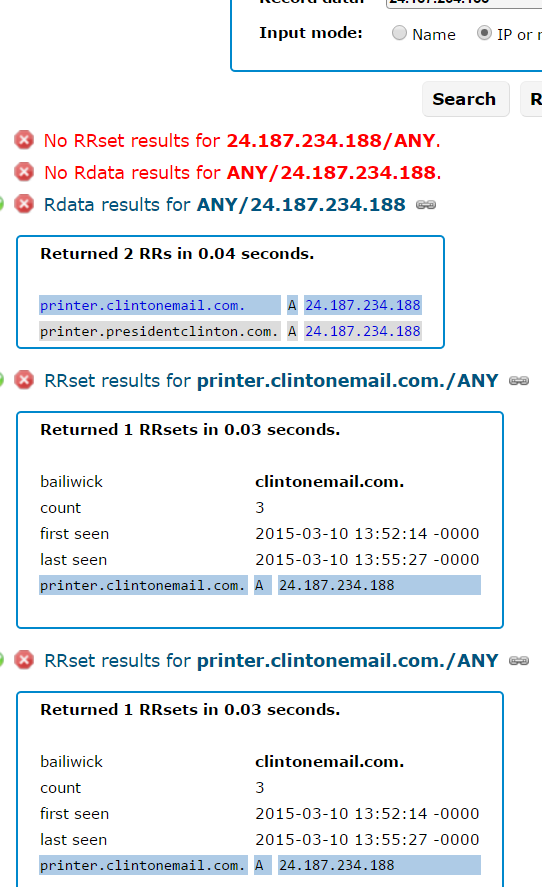
The Associated Press today points to a remarkable footnote in a recent State Department inspector general report on the Hillary Clinton email scandal: The mail was managed from the vanity domain “clintonemail.com.” But here’s a potentially more explosive finding: A review of the historic domain registration records for that domain indicates that whoever built the private email […]