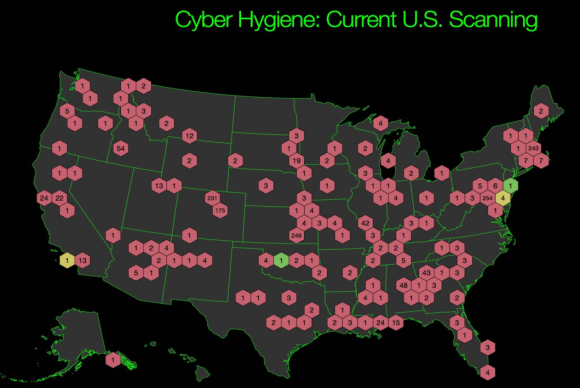
The U.S. Department of Homeland Security (DHS) has been quietly launching stealthy cyber attacks against a range of private U.S. companies — mostly banks and energy firms. These digital intrusion attempts, commissioned in advance by the private sector targets themselves, are part of a little-known program at DHS designed to help “critical infrastructure” companies shore up their computer and network defenses against real-world adversaries. And it’s all free of charge (well, on the U.S. taxpayer’s dime).
KrebsOnSecurity first learned about DHS’s National Cybersecurity Assessment and Technical Services (NCATS) program after hearing from a risk manager at a small financial institution in the eastern United States. The manager was comparing the free services offered by NCATS with private sector offerings and was seeking my opinion. I asked around to a number of otherwise clueful sources who had no idea this DHS program even existed.
DHS declined requests for an interview about NCATS, but the agency has published some information about the program. According to DHS, the NCATS program offers full-scope penetration testing capabilities in the form of two separate programs: a “Risk and Vulnerability Assessment,” (RVA) and a “Cyber Hygiene” evaluation. Both are designed to help the partner organization better understand how external systems and infrastructure appear to potential attackers.
“The Department of Homeland Security (DHS) works closely with public and private sector partners to strengthen the security and resilience of their systems against evolving threats in cyberspace,” DHS spokesperson Sy Lee wrote in an email response to an interview request. “The National Cybersecurity Assessments and Technical Services (NCATS) team focuses on proactively engaging with federal, state, local, tribal, territorial and private sector stakeholders to assist them in improving their cybersecurity posture, limit exposure to risks and threats, and reduce rates of exploitation. As part of this effort, the NCATS team offers cybersecurity services such as red team and penetration testing and vulnerability scanning at no cost.”
The RVA program reportedly includes scans the target’s operating systems, databases, and Web applications for known vulnerabilities, and then tests to see if any of the weaknesses found can be used to successfully compromise the target’s systems. In addition, RVA program participants receive scans for rogue wireless devices, and their employees are tested with “social engineering” attempts to see how employees respond to targeted phishing attacks.
The Cyber Hygiene program — which is currently mandatory for agencies in the federal civilian executive branch but optional for private sector and state, local and tribal stakeholders — includes both internal and external vulnerability and Web application scanning.
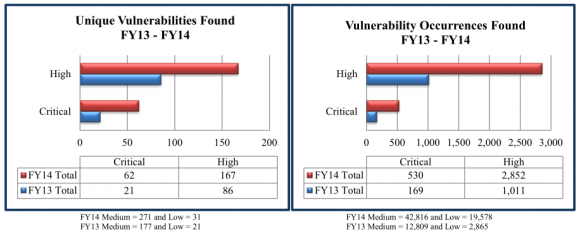
The reports show detailed information about the organization’s vulnerabilities, including suggested steps to mitigate the flaws. DHS uses the aggregate information from each client and creates a yearly non-attributable report. The FY14 End of Year report created with data from the Cyber Hygiene and RVA program is here (PDF).
Among the findings in that report, which drew information from more than 100 engagements last year:
-Manual testing was required to identify 67 percent of the RVA vulnerability findings (as opposed to off-the-shelf, automated vulnerability scans);
-More than 50 percent of the total 344 vulnerabilities found during the scans last year earned a severity rating of “high” (4o percent) or “critical” (13 percent).
-RVA phishing emails resulted in a click rate of 25 percent.
ANALYSIS
I was curious to know how many private sector companies had taken DHS up on its rather generous offers, since these services can be quite expensive if conducted by private companies. In response to questions from this author, DHS said that in Fiscal Year 2015 NCATS provided support to 53 private sector partners. According to data provided by DHS, the majority of the program’s private sector participation come from the financial services and energy sectors — typically at regional or smaller institutions.
DHS has taken its lumps over the years for not doing enough to gets its own cybersecurity house in order, let alone helping industry fix its problems. In light of its past cybersecurity foibles, the NCATS program on the surface would seem like a concrete step toward blunting those criticisms.
I wondered how someone in the penetration testing industry would feel about the government throwing its free services into the ring. Dave Aitel is chief technology officer at Immunity Inc., a Miami Beach, Fla. based security firm that offers many of the same services NCATS bundles in its product.
Aitel said one of the major benefits for DHS in offering NCATS is that it can use the program learn about real-world vulnerabilities in critical infrastructure companies.
“DHS is a big player in the ‘regulation’ policy area, and the last thing we need is an uninformed DHS that has little technical expertise in the areas that penetration testing covers,” Aitel said. “The more DHS understands about the realities of information security on the ground – the more it treats American companies as their customers – the better and less impactful their policy recommendations will be. We always say that Offense is the professor of Defense, and in this case, without having gone on the offense DHS would be helpless to suggest remedies to critical infrastructure companies.”
Of course, the downsides are that sometimes you get what you pay for, and the NCATS offering raises some interesting questions, Aitel said.
“Even if the DHS team doing the work is great, part of the value of an expensive penetration test is that companies feel obligated to follow the recommendations and improve their security,” he said. “Does the data found by a DHS testing team affect a company’s SEC liabilities in any way? What if the Government gets access to customer data during a penetration test – what legal ramifications does that have? This is a common event and pre-CISPA it may carry significant liability.”
As far as the potential legal ramifications of any mistakes DHS may or may not make in its assessments, the acceptance letter (PDF) that all NCATS customers must sign says DHS provides no warranties of any kind related to the free services. The rules of engagement letter from DHS further lays out ground rules and specifics of the NCATS testing services.
Aitel, a former research scientist at the National Security Agency (NSA), raised another issue: Any vulnerabilities found anywhere within the government — for example, in a piece of third party software — are supposed to go to the NSA for triage, and sometimes the NSA is later able to use those vulnerabilities in clandestine cyber offensive operations.
But what about previously unknown vulnerabilities found by DHS examiners?
“This may be less of an issue when DHS uses a third party team, but if they use a DHS team, and they find a bug in Microsoft IIS (Web server), that’s not going to the customer – that’s going to the NSA,” Aitel said.
And then there are potential legal issues with the government competing with private industry.
Alan Paller, director of research at the SANS Institute, a Bethesda, Md. based security training group, isn’t so much concerned about the government competing with the private sector for security audits. But he said DHS is giving away something big with its free assessments: An excuse for the leadership at scanned organizations for not doing anything after the assessment and using the results as a way to actually spend less on security.
“The NCATS program could be an excellent service that does a lot of good but it isn’t,” Paller said. “The problem is that it measures only a very limited subset of of the vulnerability space but comes with a gold plated get out of jail free card: ‘The US government came and checked us.’ They say they are doing it only for organizations that cannot afford commercial assessments, but they often go to organizations that have deep enough pockets.”
According to Paller, despite what the NCATS documents say, the testers do not do active penetration tasks against the network. Rather, he said, they are constrained by their rules of engagement.
“Mostly they do architectural assessments and traffic analysis,” he said. “They get a big packet capture and they baseline and profile and do some protocol analysis (wireless).”
Paller said the sort of network architecture review offered by DHS’s scans can only tell you so much, and that the folks doing it do not have deep experience with one of the more arcane aspects of critical infrastructure systems: Industrial control systems of the sort that might be present in an energy firm that turns to NCATS for its cybersecurity assessment.
“In general the architectural reviews are done by younger folks with little real world experience,” Paller said. “The big problem is that the customer is not fully briefed on the limitations of what is being done in their assessment and testing.”
Does your organization have experience with NCATs assessments? Are you part of a critical infrastructure company that might use these services? Would you? Sound off in the comments below.
Source: Krebs