Amazon has added multi-factor authentication to help customers better secure their accounts from hackers. With this new feature enabled, thieves would have to know your username, password, and have access to your mobile device or impersonate you to your mobile provider in order to hijack your Amazon account. The security feature allows users to receive a one-time code via text message, automated phone call, or third-party app — such as Google Authenticator.
Multi-factor authentication, also often called “two-step” or “two factor” authentication, is a great way to improve the security of your various online accounts (where available). With multi-factor logins enabled, even if thieves somehow steal your account username and password they’ll still need access to the second factor — your mobile phone — to successfully hijack your account.
Users can instruct Amazon to “remember” each device, which disables future prompts for the second factor on that device going forward. If Amazon later detects a login attempt from a device it does not recognize as associated with that account, it will prompt for the code from the second factor — text message, voice call, or app (whichever you choose).
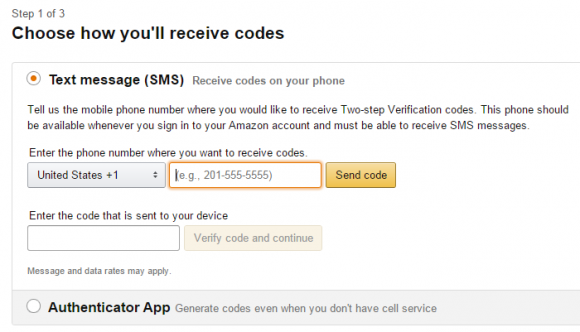
I’m not sure I succeeded the first time I tried to set up multi-factor authentication on Amazon. I signed in, clicked “Your Account,” and then under “Account Settings” clicked “Change Account Settings.” That page allowed me to add a mobile number by typing in a code that was sent to my mobile. But when I hit “Done” and went back to Amazon’s home page, I decided to revisit the page only to discover that there are two more steps needed to finish setting up multi-factor authentication.
In step two, Amazon asks for a backup phone number where users can receive text messages or voice calls, in case you don’t have access to the mobile device added in Step 1. The backup method also can be Google’s Authenticator App.
Step three just explains how it all works and allows users to skip future one-time codes on personal devices.
If you shop at Amazon, take a few minutes today to turn on multi-factor authentication for your account. While you’re at it, check out twofactorauth.org to see if multi-factor is available for other any online services you may use. Also, consider whether you’re able to beef up the security of the backup email accounts you use for your recovery address.
One final note: Receiving one-time codes by a third-party mobile app that does not require a working connection to the Internet — such as Google Authenticator — allows for fewer chances that your one-time codes could be diverted by attackers: Thieves can still call in to your Internet service provider or mobile provider, pretend to be you, and have your calls and/or texts forwarded to another number that they control.
Source: Krebs