You know you’re getting old when you can’t remember your own birthday (a reader tipped me off). Today is the sixth anniversary of this site’s launch! KrebsOnSecurity turns 6! I’m pretty sure that’s like middle age in Internet years. Absolutely none of this would be possible without you, Dear Reader. You have supported, encouraged and […]
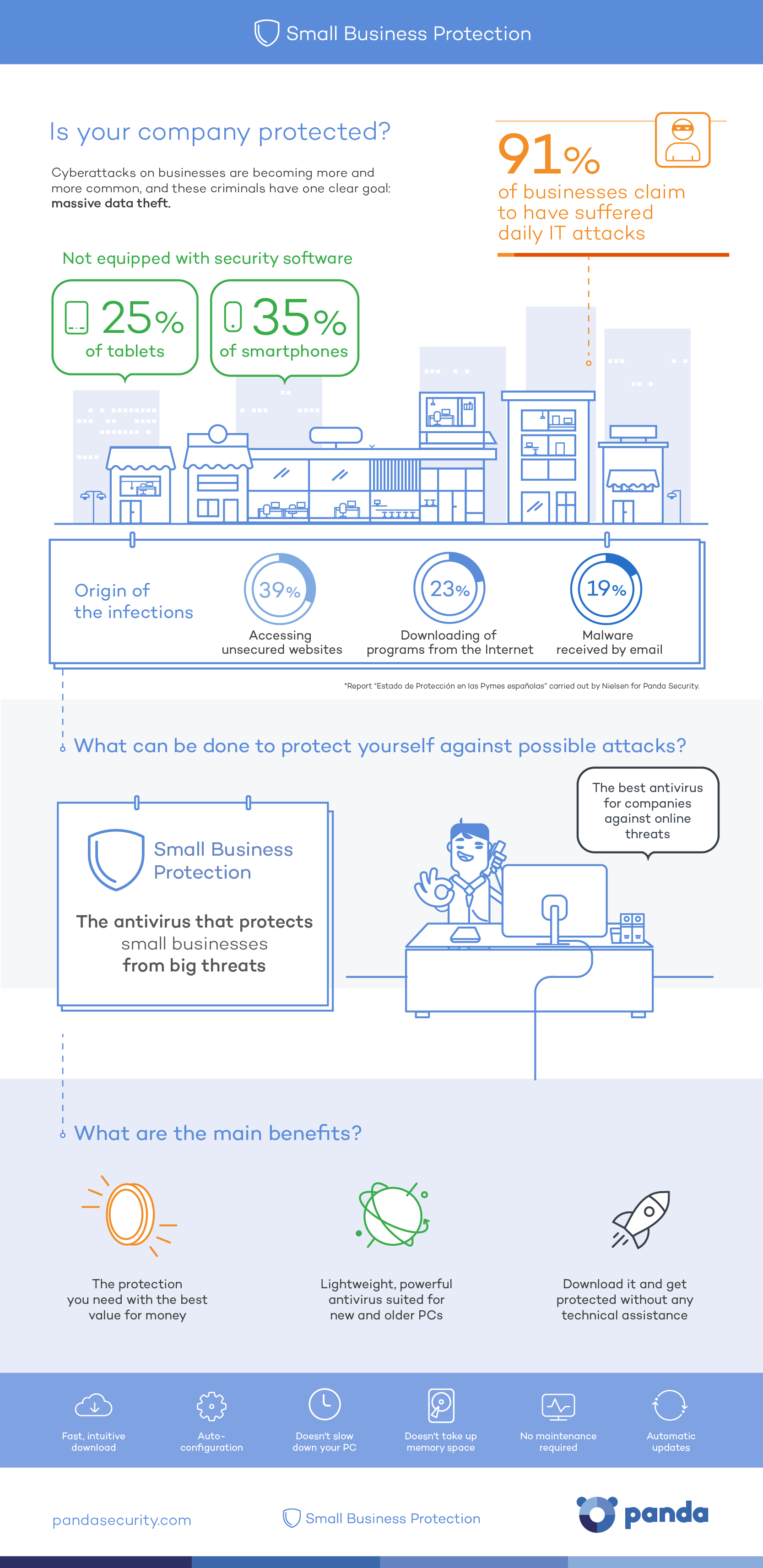
We’ve noticed that the targets of cybercriminals are growing beyond private users and large corporations. Freelancers and microbusinesses are suffering daily attacks as they are an easy target for the bad guys and represent nearly 80% of the business sector in USA. Thus, Panda Security has designed a tailor-made solution: Small Business Protection. An antivirus […]
What do you think when you receive yet another spam or phishing message on your mobile phone? Most likely it is: “Who are these people, and how on earth did they get my phone number?” Initially, suspicion usually falls on an unscrupulous employee at some organization that you gave your number to. However, it’s not […]
Adobe has shipped a new version of its Flash Player browser plugin to close at least 19 security holes in the program, including one that is already being exploited in active attacks. The new Flash version, v. 20.0.0.267 for most Mac and Windows users, includes a fix for a vulnerability (CVE-2015-8651) that Adobe says is […]
My PayPal account was hacked on Christmas Eve. The perpetrator tried to further stir up trouble by sending my PayPal funds to a hacker gang tied to the jihadist militant group ISIS. Although the intruder failed to siphon any funds, the successful takeover of the account speaks volumes about why most organizations — including many financial institutions — remain […]
Following a spate of security breaches and concerns, Apple has taken the steps to ensure that 2016 doesn’t see a repeat of the software problems that it suffered in recent months. The security measures have been widespread, with updates to their operating systems for mobile (iOS) and Mac (OS X), its television service (Apple TV), […]
Hyatt Hotels Corporation said today it recently discovered malicious software designed to steal credit card data on computers that operate the payment processing systems for Hyatt-managed locations. Hyatt’s notice to customers has very few details about the investigation, such as how long the breach lasted or how many consumers may have had their card data […]
On the eve of major holidays such as Christmas and New Year, mail and delivery services face a dramatic increase in the amount of shipments they have to handle. People are buying far more goods online than usual, looking for bargains in the sales, and sending gifts by mail – both nationally and internationally – […]
Software vulnerabilities are one of those problems that potentially affect all users. A vulnerability is a fault in a program’s implementation that can be used by attackers to gain unauthorized access to data, inject malicious code or put a system out of operation. In most cases, vulnerabilities arise from a lack of attention to fine […]