Microsoft releases 11 Security Bulletins (MS15-032 through MS15-042) today, addressing a list of over 25 CVE-identified vulnerabilities for April of 2015. Critical vulnerabilities are fixed in Internet Explorer, Microsoft Office, and the network and graphics stacks. Most of the critical remote code execution (RCE) vulnerabilities reside in the IE memory corruption bugs for all versions of Internet […]
How great would it be if we could walk into a store and buy cyber security off the shelf? Such convenience is a dream, but we can all dream, can’t we? However, cyber security cannot be bought as described above, but must be taught. This brings us to the inherent threat in organizations – the […]
As we can see, cybercriminals are relentless in their pursuit of quick money, and at the same time creating fear in us. Dyre Wolf, named by IBM Security researchers, is a variant of Dyre Trojan which first made its appearance in June 2014. It has been used in a succession of phishing campaigns across the […]
DDoS attacks are the rise. In 2014, attacks almost doubled compared to that of the year before, and it does not seem to abate.Dos or DDoS attacks are more than just causing servers to be unavailable to users. Many attackers are using DDoS attacks to steal information and money as well. First, let’s look at the […]
A new Trojan specifically targeting the energy sector has been found. Trojan.Laziok is being used to compromise energy sector companies in a multi-staged targeted attack. This Trojan also acts as a reconnaissance tool, which means that it will gather information on the systems and then tailor the attack methods. The malware will then identify the […]
Macro viruses are making a comeback! Here’s a little bit of history on macro viruses. Back in the 90s, macro viruses were a cause for concern. It became a thorn in the sides of computer users, infecting many PCs running Microsoft Word and Excel. A macro virus is a computer virus that replaces a macro. […]
The infamous Vawtrak banking Trojan has reared its ugly head with new features that make it more dangerous than it previously was. It allows data to be sent and received data through encrypted favicons (see Definition) via the secured Tor network, which is a hidden web service. Why it become so dangerous? It’s because the […]
BREAKING NEWS! Fact: Software vulnerabilities are growing and that security gaps should be closed faster. However, this is a not always the case. It’s for this reason that cybercriminals seem to be ahead of the game, find the loopholes and infiltrate computer systems of unsuspecting users. Think zero-day attacks (see Definition). Sometimes, security patches from […]
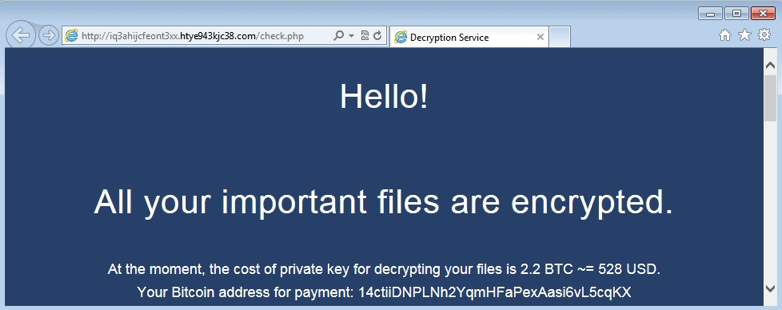
We have written or about ransomware in previous Advisories. In this edition we are revisiting ransomware because this menace is not going away anytime soon. In fact, the proliferation of ransomware is getting more aggressive. Why wouldn’t it? In this case the road to riches is paved with money or ramsom – yours. Unfortunately, ransomware […]