Embracing eConfirm.my: The Experience Thus Far Early adopters recommend that their peer audit firms adopt this electronic bank confirmation platform, as the pros outweigh the cons. In June 2020, the Malaysian Institute of Accountants (MIA) officially launched the industry-wide Electronic Bank Confirmation (EBC) Platform (eConfirm.my) together with platform developer and service provider, Extol Corporation Sdn […]
The Malaysian Institute of Accountants (MIA) announced today that eConfirm.my, the first Industry-wide Electronic Bank Confirmation Platform in Malaysia, is scheduled to go live on a staggered basis throughout the month of May 2020, beginning on 5 May 2020. eConfirm.my will help audit firms to eliminate the need for paper-based confirmations, expedite bank confirmations and […]
The security firm Intezer reported it had successfully shut down 15 active ransomware campaigns using the eCh0raix or QNAPCrypt variant with denial of service attacks. NAS servers normally store large amounts of important data and files, which make them a valuable target for attackers and especially a viable target for ransomware campaigns. In a rare […]
In a rare occurrence, the American National Security Agency (NSA) has published a statement urging people to update their older Windows systems to protect against the BlueKeep vulnerability. The NSA referenced “growing threats” and noted that BlueKeep “is the type of vulnerability that malicious cyber actors frequently exploit through the use of software code that […]
Under very specific conditions, code running in a Docker container could access files anywhere on a server, according to a new CVE. In an unusual progression of events, the vulnerability and exploits have been disclosed before patches are available. The vulnerability, designated CVE-2018-15664, was discovered by researcher Aleka Sarai. A flaw in the Docker “cp” command, which […]
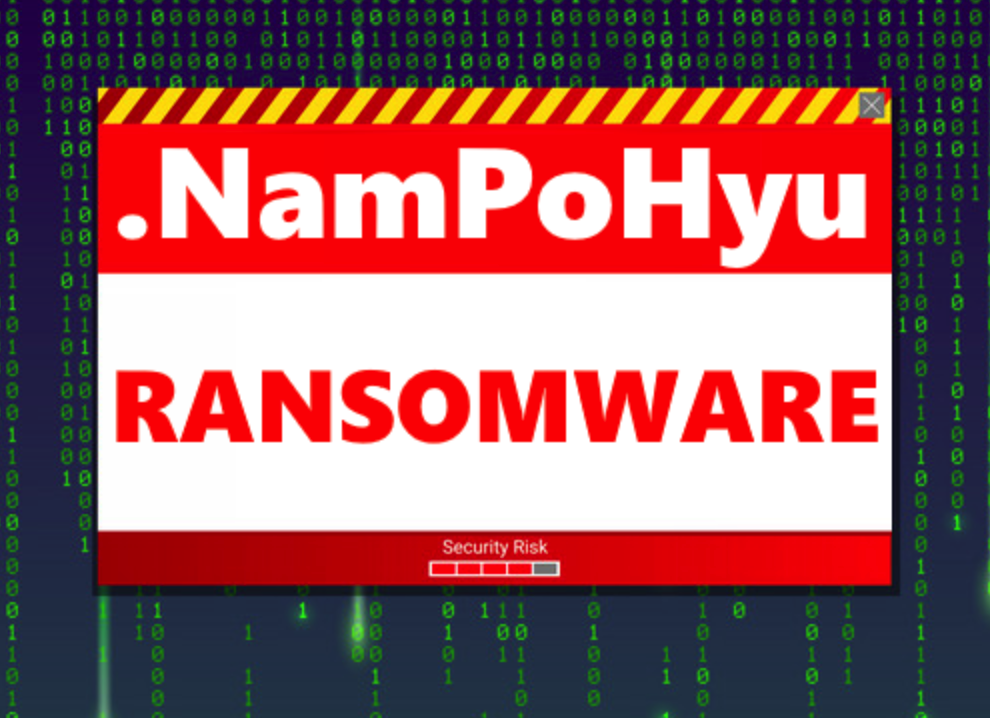
The NamPoHyu ransomware is doing things differently by searching for accessible Samba servers, brute forcing the passwords, and then remotely encrypting their files and creating ransom notes. A ransomware family was recently spotted targeting vulnerable Samba servers: NamPoHyu Virus aka MegaLocker Virus. NamPoHyu Virus is unlike typical ransomware families that are delivered locally and launched as executables. Instead, […]
On April 9, Windows released its latest update which seems to be causing some problems with anti malware software. As of time of publication the brands affected by the patch are Sophos, Avira, ArcaBit, Avast, and most recently McAfee. Windows April 9th Patch Tuesday Windows 7, 8.1, Server 2008 R2, Server 2012, and Server […]
At least 27 universities in the United States, Canada and countries in the Southeast Asian region was reportedly targeted by Chinese hackers looking for information relating to the maritime military technologies to steal. An article from the Wall Street Journal revels that a substantial list of university targets that reflects an elaborate scheme, dates back […]
Let’s Encrypt certificates can now stand on their own for almost all newer versions of operating systems, browsers and devices. Microsoft has added direct trust for Let’s Encrypt certificates, meaning that all major browsers and operating systems, including Apple, Blackberry, Google, Microsoft, Mozilla and Oracle, now all directly trust the Let’s Encrypt root, ISRG Root […]
The new strategy allows an attacker to instead lift ID information directly from the router, within minutes. Legacy Wi-Fi just became a little less safe: According to Jens Steube, the developer of the password-cracking tool known as Hashcat, has found a faster, easier way to crack WPA/WPA2-protected Wi-Fi networks. Hackers have compromised the WPA/WPA2 encryption […]