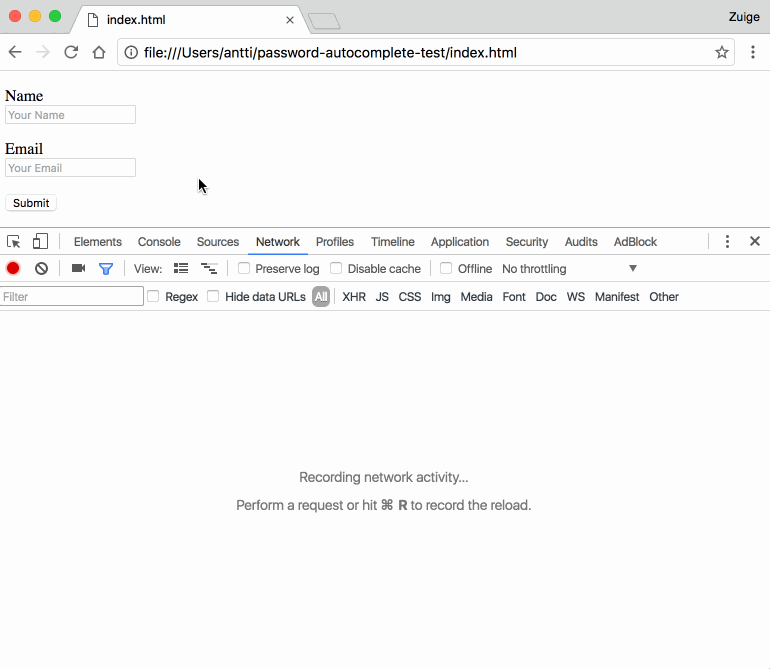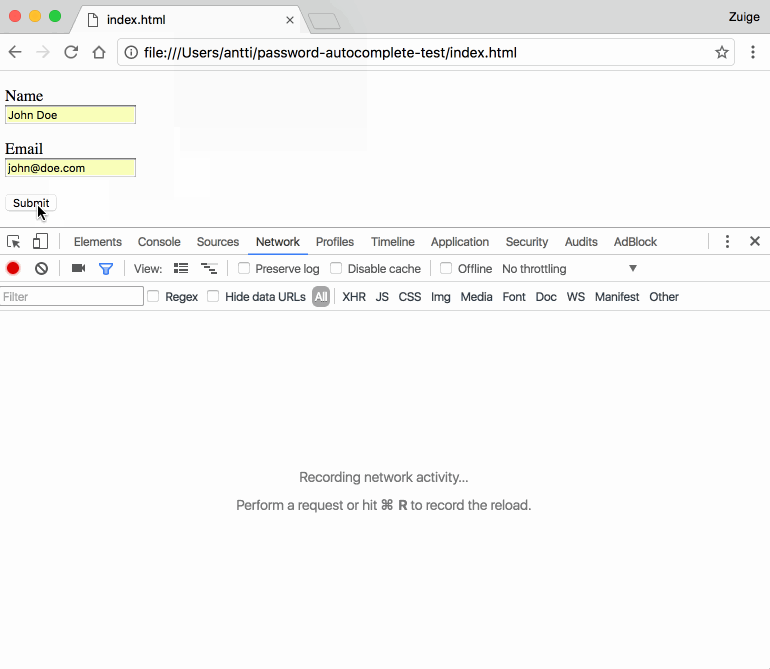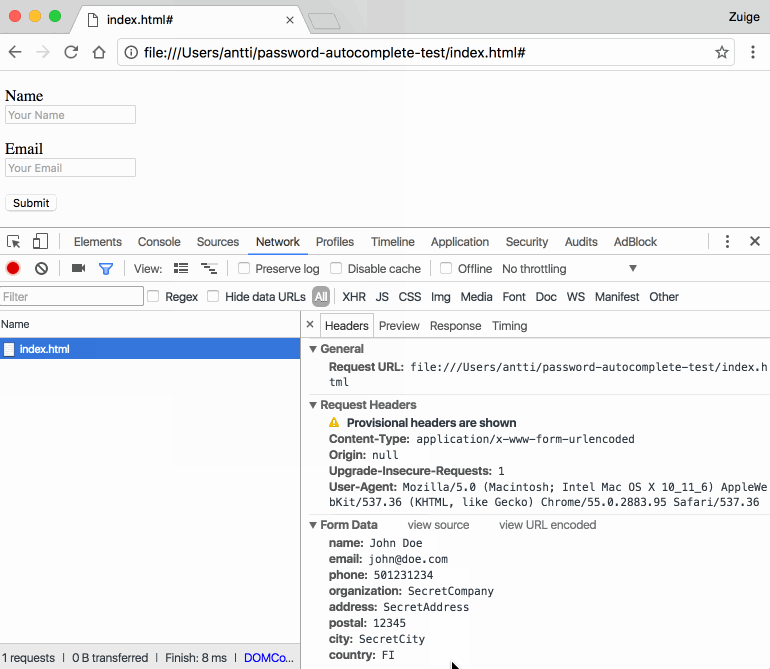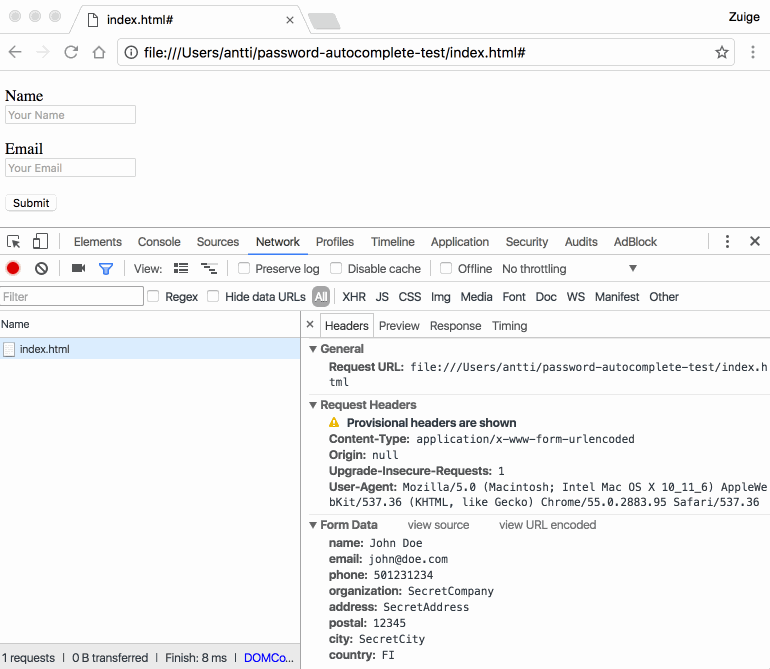
The autofill feature that many browsers offer is a useful time-saving tool that saves you from having to manually fill out forms with the same information every time. Programs include all the necessary information without the user having to go from one field to another to write information that is often repeated in most […]
The following is a compilation of all past PandaLabs reports. It is a complete record of the cybersecurity lab’s highlights. 2016 Informe Q1 Informe Q2 Informe Q3 Annual Report 2015 Q1 Report Q2 Report Q3 Report Annual Report 2014 Q1 Report Q2 Report Q3 Report Annual Report 2013 Q1 Report Q2 Report Q3 Report Annual Report […]
When talking about cybersecurity, we instantly think of viruses and malware. But advances in personal computer security have made it much harder for hackers to infect your PC through traditional channels like email. As a result, they have developed new attack methods to get around your defences using a range of techniques, on and off-line. […]
In recent months, there’s been a significant uptick in PandaLabs reports of malware that is installed using a Remote Desktop Protocol (RDP). Every day, we witness thousands of infection attempts using ransomware, hijacking systems for bitcoin mining, etc., which all have one thing in common: access via RDP after gaining entry with credentials obtained using […]
Around July last year, more than a 100 Israeli servicemen were hit by a cunning threat actor. The attack compromised their devices and exfiltrated data to the attackers’ command and control server. In addition, the compromised devices were pushed Trojan updates, which allowed the attackers to extend their capabilities. The operation remains active at the […]
Mobile gaming is changing the shape of online gaming but how safe is it? Mobile gaming is huge! According to a report recently released by market research firm SuperData, the global mobile gaming sales revenue in 2016 was over $40 billion. The mobile gaming market is now bigger than the global tea market and the […]
You arrive at the office, you approach the security gates, you swipe your card and start the day. It’s one of the motions that a large percentage of the workforce goes through daily, because today, and it seems that for a while yet, the access card is still the reigning security device for entering […]
The new European General Data Protection Regulations came into effect on 25 May, although countries and institutions have a period of two years to prepare for their final implementation. Given this situation, and to comply with the requirements of the standard, one would hope for companies to increase their investment in computer security. However, the […]
Online dating fraud victims at record high The rise of online dating has been phenomenal. In fact, a research paper published by the Association for Psychological Research found that online dating services are now the second most popular way for people to find love. For those hoping to begin a romantic relationship this is great […]
Will robots steal jobs? For many, the answer is yes, they will indeed. A recent study from the World Economic Forum has put a number on the dispute that has been on the table for a while now: between now and 2020, 7.1 million jobs will disappear in advanced countries, and 2.1 million will be […]