Your daily round-up of some of the other stories in the news Source: Sophos
A recent indie horror film called It Follows explores an interesting moral grey area. In that film a shape-shifting creature slowly but unstoppably chases a victim. This victim -who faces the inevitable prospect of being worn down and caught- can pass on this curse to someone else by sleeping with them. The question the film […]
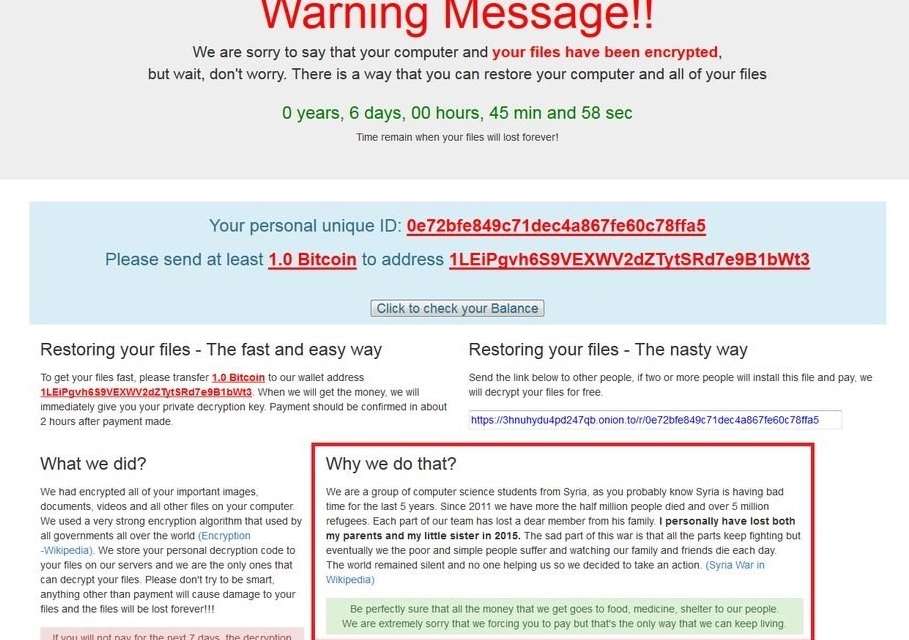
Ransomware is one of the most frequent forms of cyberattack that a company can face. Through an infected email or by some other means, criminals can lock a computer, encrypt files, or sequester an entire corporate network. The main goal: ransom money, usually in the form of cryptocurrency, in exchange for freeing up the virtually […]
The printer you have in your office may be less innocent than you thought. Some experts have already shown that they can even become a steganographic tool, the art, well-known in computer security, of hiding information from prying eyes. A few years ago, the Electronic Frontier Foundation, an organization that defends civil liberties on the […]
Many businesses are actively encouraging their employees to use social media at work, hoping that they will become “brand advocates”, talking about the company’s products and services. Employers also hope that their worker’s accounts will help to give the company a “human” face. But as good as these intentions are, you should carefully consider whether […]
Last year is proof that stories about Kim Kardashian and Pikotaro’s PPAP song were not the only things able to break the internet, 2016 was a year full of news about data breaches, stolen sensitive information, hackers extortion and DDoS attacks that in some cases had a significant impact on the lives of many Americans. […]
This February, from the 13th to the 17th, the XXII Edition of the RSA Conference, the largest event of cyber security in the world, will be held at the San Francisco Moscone Center. Major companies, suppliers and cybersecurity gurus will gather to find solutions to their business concerns and discuss industry trends — an incomparable […]
The next revolution in computer science already has a name: quantum computing. Computers capable of working with the superposition of ones and zeros (using qubits, which can take both values, unlike bits, which take one or the other) are still a laboratory animal, but research is increasingly approaching the dream of developing a machine with […]