It was the last weekend of May and just like every year, hackers, forensic experts and pentesters met at the Universal Hall in Berlin for the BerlinSides conference. ‘A con from hacker for hacker’. This years motto is ‘electrifying’ and the badges and shirts show the picture of Nikola Tesla. BerlinSides is the successor of […]
One of the best things about Android’s operating system is the variety of options available with dozens of manufacturers from all backgrounds, hundreds of models on the market, prices for all budgets and features for all tastes. However, the same breadth and depth of product and service offerings which makes Android attractive is, at the same time, one of their […]
We’re sure your browser has been hijacked before. Say you decide to download a program you need from a seemingly reliable website (like Softonic), and you click “install” to begin downloading without really thinking about it. When it finishes downloading, you go back to the browser and you realize that one or more toolbars have […]
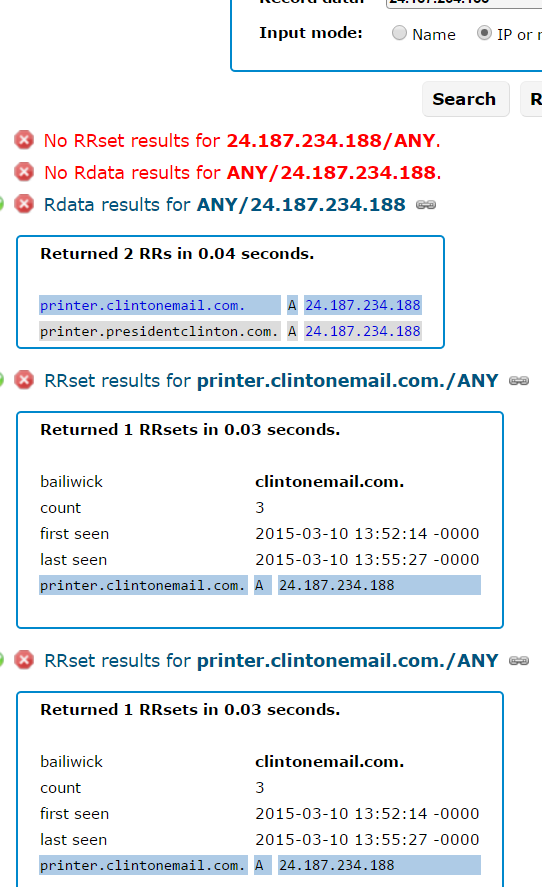
The Associated Press today points to a remarkable footnote in a recent State Department inspector general report on the Hillary Clinton email scandal: The mail was managed from the vanity domain “clintonemail.com.” But here’s a potentially more explosive finding: A review of the historic domain registration records for that domain indicates that whoever built the private email […]
Mobile phones. Nowadays, they are our constant companions, our confidants. They know everything about our everyday lives. Every day, whether we’re on our way to or from work or just wandering around the city, mobile phones collect this information. We take photos, share our impressions on social networks, send work and non-work related mails, text […]
Every type of person is a PayPal person. Each day, hundreds of well-known investors and business magnates are added to the list, like Peter Thiel, one of the original Facebook investors, or the South African tycoon Elon Musk, who is the CEO of both Tesla and SpaceX. A good part of the internet already uses […]
Recent local news stories about credit card skimmers found in self-checkout lanes at some Walmart locations reminds me of a criminal sales pitch I saw recently for overlay skimmers made specifically for the very same card terminals. Much like the skimmers found at some Safeway locations earlier this year, the skimming device pictured below was designed […]
CVE-2015-2545 is a vulnerability discovered in 2015 and corrected with Microsoft’s update MS15-099. The vulnerability affects Microsoft Office versions 2007 SP3, 2010 SP2, 2013 SP1 and 2013 RT SP1. The error enables an attacker to execute arbitrary code using a specially crafted EPS image file. The exploit uses PostScript and can evade Address Space Layout […]