Fit-bracelets, smart-watches, and other wearable technology have joined the “Internet of Things”, everyday objects that collect and exchange information (think: vehicles, smart thermostat systems, and any other device with online capabilities). But did you know that there are much more advanced, health-monitoring, devices out there? The high-tech pacemakers made today have a ton of benefits, especially for […]
The word that scared all Google users last summer is back and worse than ever. Stagefright, nicknamed by its founder Metaphor, is even more dangerous in its new version. Much like its name’s meaning, Stagefright, hides deep in the Android library, unnoticeable to Android users as they watch videos of cute puppies and crafty DIY […]
In order to secure and maintain an IT infrastructure, it is vital to know what is going on in the network that the Endpoint is running on. This means that managers and other stakeholders need to know if something unusual is happening within the corporate network. When we use the word “unusual” we mean […]
Verizon Enterprise Solutions, a B2B unit of the telecommunications giant that gets called in to help Fortune 500’s respond to some of the world’s largest data breaches, is reeling from its own data breach involving the theft and resale of customer data, KrebsOnSecurity has learned. Earlier this week, a prominent member of a closely guarded underground […]
Many U.S. citizens are bound to experience delays in getting their tax returns processed this year, thanks largely to more stringent controls enacted by Uncle Sam and the states to block fraudulent tax refund requests filed by identity thieves. A steady drip of corporate data breaches involving phished employee W-2 information is adding to the backlog, as is […]
One of the most complex tasks for the cybercriminals is to ensure their malicious code goes undetected by antivirus and achieves its goal. For this, they have invested a lot on more complex infection processes, going beyond the traditional phishing and using techniques where the malicious payload is hidden in encrypted files – even using […]
The year 2016 started with a quite a number of security incidents related to hacks of hospitals and medical equipment. They include a ransomware attack on a Los Angeles hospital, the same in two German hospitals, a case of researchers hacking a patient monitor and drug dispense system, an attack on a Melbourne hospital and […]
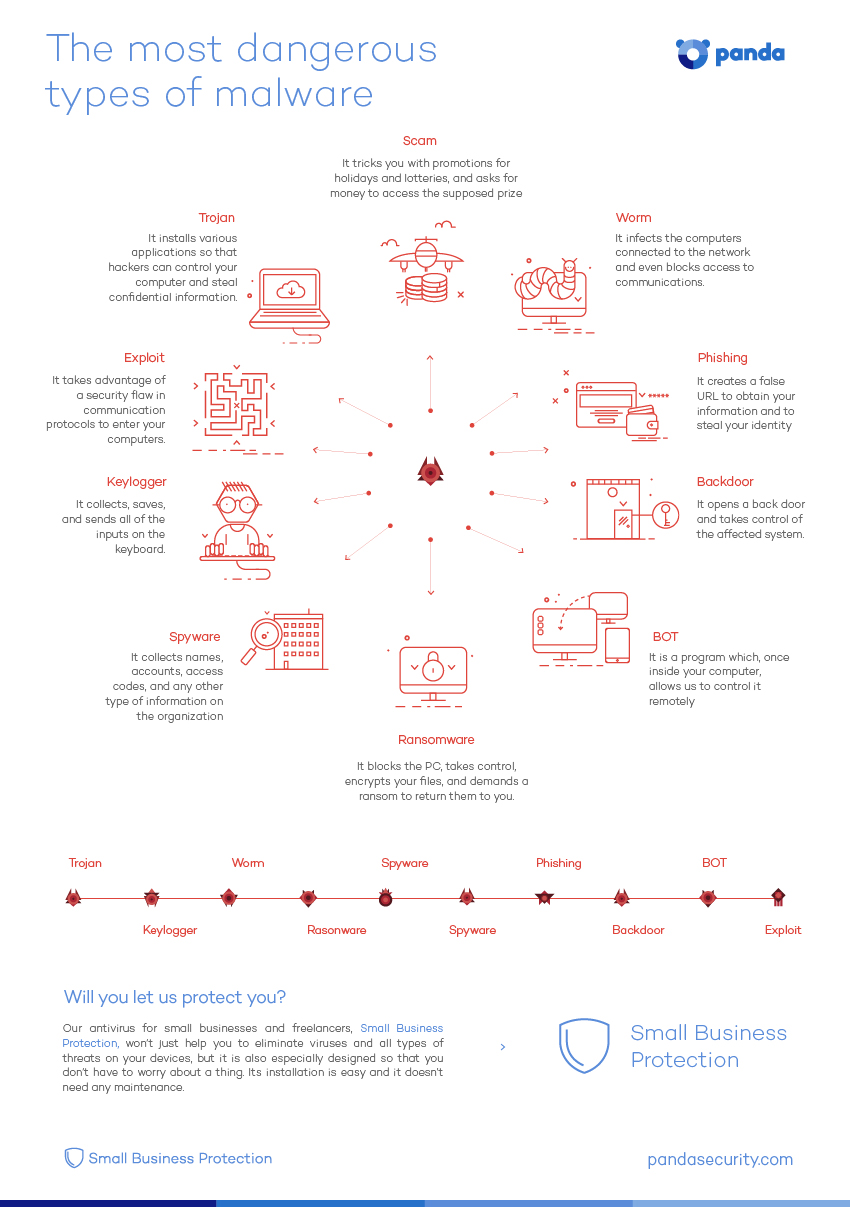
Since the beginning of the internet, there have been hackers who have used the Net to benefit at the expense of other users. Some have managed to attack so many people, or companies and institutions so large, that they have become internationally infamous. These are the great villains of the internet. At Panda Security, […]