At the end of last year, the US government put an end to the secret surveillance program carried out by the National Security Agency (NSA). Not bad. Apparently, citizens have one less reason to worry about the privacy of their phone calls. However, the suspicion that someone else is listening to your conversations not only […]
Download the full report (PDF) With astonishing annual revenues of over a hundred billion dollars, the gaming industry has in the past been compared to Hollywood’s burgeoning business, repeatedly demonstrating the influence behind its ever expanding and loyal fan base. Having an endless list of “big hit” video-games coexisting peacefully with humble but still fun-filled […]
It’s remarkable how quickly a stolen purse or wallet can morph into full-blown identity theft, and possibly even result in the victim’s wrongful arrest. All of the above was visited recently on a fellow infosec professional whose admitted lapse in physical security led to a mistaken early morning arrest in front of his kids. The guy […]
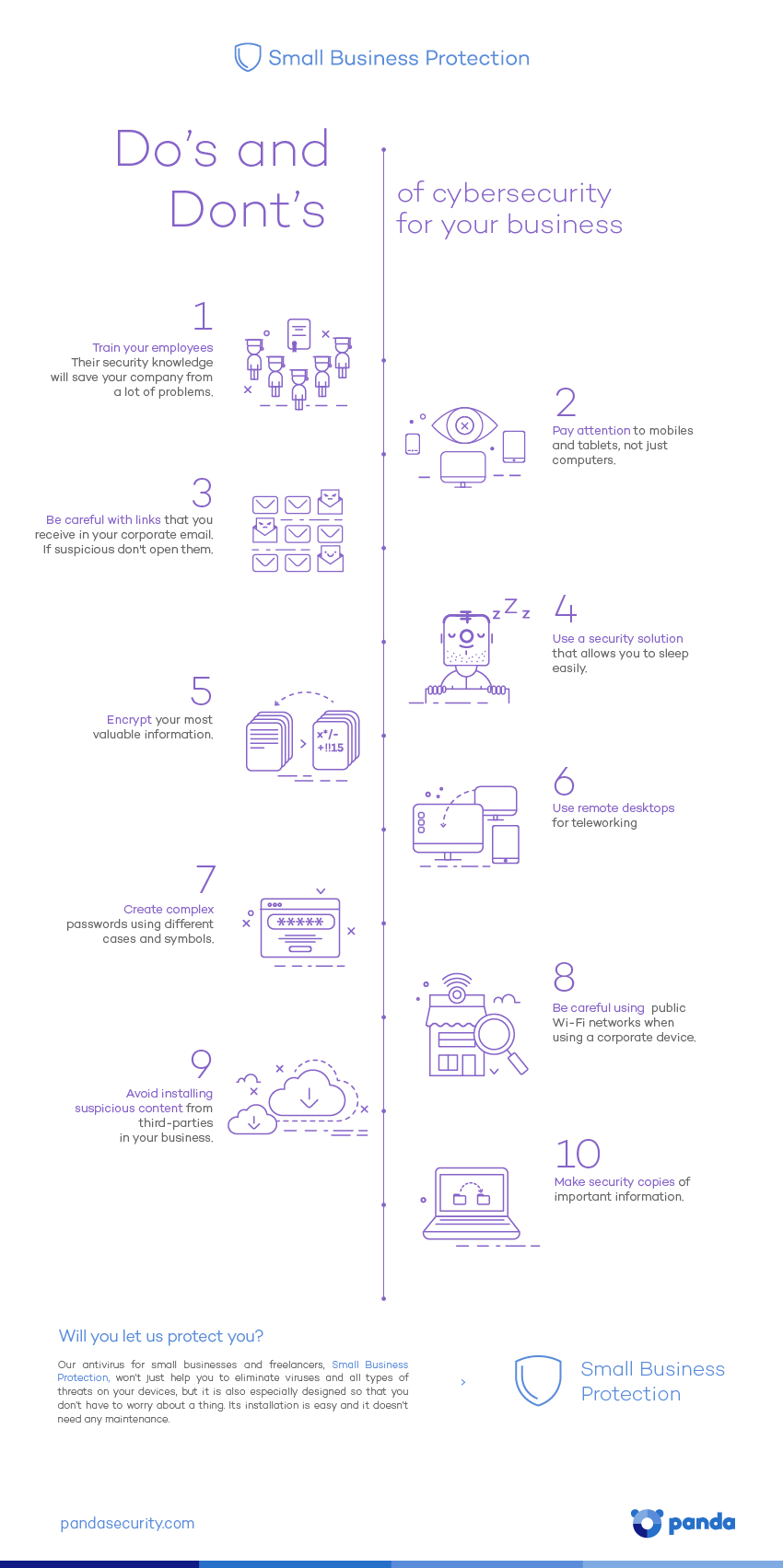
Do’s and Don’ts of cybersecurity for your business Train your employees. Their security knowledge will save your company from a lot of problems. Pay attention to mobiles and tablets, not just computers. Be careful with links that you receive to your corporate mail – don’t open them. Use a security solution that allows you […]
Get ready for this: Soon, selfies will not only be a good way to record the passing of time upon your face everywhere you go. As physical features are unique of each person, they will also be used as credit card passwords. At least that’s what credit card firm MasterCard thinks. The company announced at […]
Staminus Communications Inc., a California-based Internet hosting provider that specializes in protecting customers from massive “distributed denial of service” (DDoS) attacks aimed at knocking sites offline, has itself apparently been massively hacked. Staminus’s entire network was down for more than 20 hours until Thursday evening, leaving customers to vent their rage on the company’s Facebook and […]
It happens that malware writers and other miscreants in the digital world put messages in their malware. Sometimes they do it just for the “lulz”, sometimes to insult a person who hampers their criminal business, sometimes to deliver information to the guys on the other side who oppose them. We hope the case described in […]
A few months ago, Apple devices were the victim of a large-scale cyber-attack, the largest in the company’s history. The company had to withdraw more than 50 iPhone, iPad and Mac apps from the App Store as they installed malicious software that allowed criminals to control users’ devices remotely and steal personal information. So you […]
User-friendly and secure. Hardly anyone would pick either word to describe the vast majority of wireless routers in use today. So naturally I was intrigued a year ago when I had the chance to pre-order a eero, a new WiFi system billed as easy-to-use, designed with security in mind, and able to dramatically extend the […]