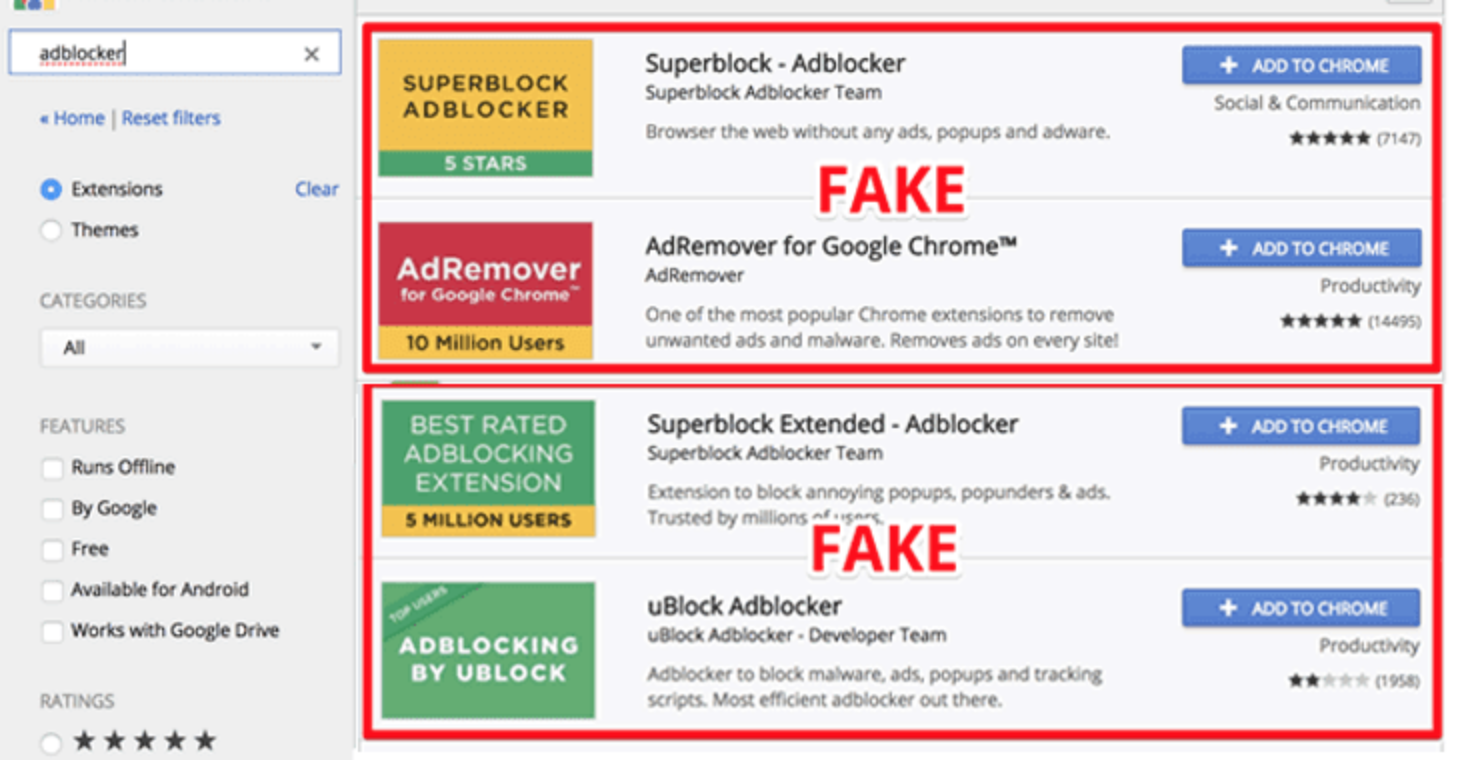
If you have installed any of the below-mentioned Ad blocker extension in your Chrome browser, you could have been hacked. A security researcher has spotted five malicious ad blockers extension in the Google Chrome Store that had already been installed by at least 20 million users. Unfortunately, malicious browser extensions are nothing new. They often […]
For three years running, cybersecurity has remained the top threat to businesses across multiple categories, including infrastructure, geopolitical and emerging risks. That’s according to the 11th Annual Survey of Emerging Risks, conducted by the Casualty Actuarial Society, Canadian Institute of Actuaries, and the Society of Actuaries’ Joint Risk Management Section. More than 200 risk managers, […]
Microsoft has averted a massive and widespread campaign that would have seen tens of thousands of machines impacted. The software giant reported that on March 6, “Windows Defender AV blocked more than 80,000 instances of several sophisticated Trojans that exhibited advanced cross-process injection techniques, persistence mechanisms and evasion methods.” The Trojans, which are new variants […]
Almost half of organizations do not regularly make substantial changes to their security strategy, even after experiencing a cyber-attack. That’s according to the CyberArk Global Advanced Threat Landscape Report 2018, in which the security vendor surveyed 1300 IT security decision makers to explore the current state of enterprise security practices. The general theme of the report was […]
A newly detailed mobile malware can do more than steal data from infected devices: it can also record ambient audio and send the recordings to cloud storage accounts controlled by attackers. Dubbed RedDrop, the malware can also inflict financial costs on victims by sending SMS messages to premium services, security firm Wandera says. The U.K.-based […]
The Federal Bureau of Investigation is warning businesses about a spike in phishing campaigns requesting W-2 information from payroll personnel. In a recent security advisory the FBI warned it has seen an increase since January in reports of compromised or spoofed emails involving W-2 forms. These emails, coming during the IRS’s tax filing season, can […]
Malware sophistication is increasing as adversaries begin to weaponize cloud services and evade detection through encryption, which is being used as a tool to conceal command-and-control activity. That’s according to the Cisco 2018 Annual Cybersecurity Report (ACR). It also found that while encryption is meant to enhance security, the expanded volume of encrypted web traffic […]
Google Project Zero researchers are warning of two critical remote code execution vulnerabilities in popular versions of BitTorrent’s web-based uTorrent Web client and its uTorrent Classic desktop client. According to researchers, the flaws allow a hacker to either plant malware on a user’s computer or view the user’s past download activity. Project Zero security researcher […]
A new business email compromise (BEC) campaign is targeting accounts payable personnel at Fortune 500 companies in an attempt to trick victims into initiating fraudulent wire transactions to attacker-controlled accounts, IBM warns. As part of BEC scams, attackers take over or impersonate a trusted user’s email account to target other companies and divert funds to […]
The number of reported vulnerabilities in Microsoft software has mounted from 325 in 2013 to 685 last year, a rise of 111 percent, according to new research. Moreover, there has also been a 54 percent increase in critical Microsoft vulnerabilities since 2016, researchers at Avecto said in their report, which is based on data from […]