Email scam artists last week tricked an employee at data storage giant Seagate Technology into giving away W-2 tax documents on all current and past employees, KrebsOnSecurity has learned. W-2 forms contain employee Social Security numbers, salaries and other personal data, and are highly prized by thieves involved in filing phony tax refund requests with […]
In recent weeks, we have seen several mass-mailings in French, Italian and English, imitating messages from Amazon’s online shops. In all the mailings, the recipients were offered a voucher, a gift certificate or some other prize. The enticing offers were mostly sent from Italy or France. However, the email addresses from which they were sent […]
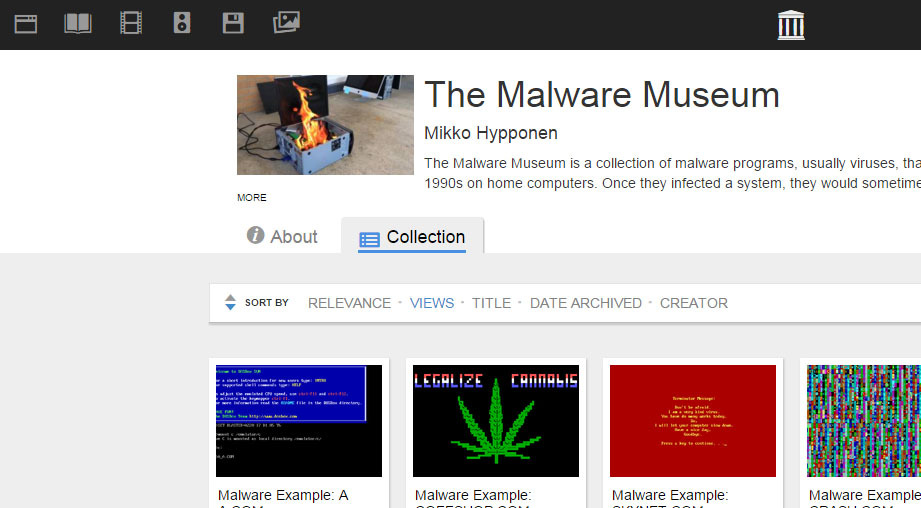
A very special museum has just opened its doors, albeit virtual ones. The gallery is online and its works aren’t paintings, nor sculptures, nor antiques: they are pieces of malware that during the 80s and 90s attacked the now defunct operating system MS-DOS (remember that?!). The collection is hosted on the pages of the Internet […]
Brazilian cybercriminals have been “competing” with their Russian-speaking “colleagues” for a while in who makes more Trojan bankers and whose are most effective. A few days ago we found a new wave of different campaigns spreading the initial “Banloader” components in Jar (Java archive), which is very particular by its nature – it’s able to […]
The main danger posed by apps that gain root access to a mobile device without the user’s knowledge is that they can provide access to far more advanced and dangerous malware with highly innovative architecture. We feared that Trojans obtaining unauthorized superuser privileges to install legitimate apps and display advertising would eventually start installing malware. […]
This week, a large fraction of the world’s top security professionals converge into the wonderful city of San Francisco for RSA Conference 2016. Spread across several halls and buildings, the event has grown to be a kind of “meet anyone” type of conference/show, where you can’t walk for more than a 100 meters without running […]
A number of credit unions say they have experienced an unusually high level of debit card fraud from the breach at nationwide fast food chain Wendy’s, and that the losses so far eclipse those that came in the wake of huge card breaches at Target and Home Depot. As first noted on this blog in […]
Thanks to their inbuilt sensors, bracelets and other wearables have become the perfect tool for monitoring our fitness and wellbeing – they inform us of our sporting progression and of how many calories we are burning at the gym. However, the growth in sales of these devices has also lead to a growth in the […]
Last week, Patrick Wardle published a nice analysis of a new Backdoor and Dropper used by HackingTeam, which is apparently alive and well. Since HackingTeam implants are built on-demand for each target, we wanted to take a closer look: to see how it works and what its functionality reveals about the possible interest of the […]
More than 400 million selfie lovers can breathe a sigh of relief – Instagram, the social network phenomenon, has revealed that the two-step verification process is soon to be unveiled on its platform. This means that Instagram accounts will now be better protected by a log-in procedure which should make things harder for cyber-attackers trying […]