Infecting computers with a new type of Ransomware
Sending out your resume into the net’s black hole can make the job application process feel hopeless. Where do our resumes end up? Do recruiters even read them? The recipe for landing a job is already a difficult task in itself, but now we have to squeeze a little more fear into it. Every time we apply for jobs, we could be falling prey to one of these new cyber-attacks that use ransomware to hold your computer hostage.
Warn those fresh-grads that they could be fresh-meat
Digital-age criminals are posing as hiring companies on various job-posting websites. The cyber-criminals are tricking both candidates and recruiters, asking them for too much information, like, credentials and economic information. Know anyone on the job hunt? Are you familiar with LinkedIn? Like we’ve stated before, these are becoming some of the best resources for cyber-criminals.
We’ve also seen these wrong-doers capture innocent job-searchers by “pretending” to be hiring managers from important companies, where they post false job advertisements so they can phish for credentials and other sensitive information. In addition to phishing, we have been advised of another type of attack: a variant of malware that black-hats are using to infect company computer systems when their recruiters download, what they think to be, a candidate’s CV.
They wanna get ya with PETYA
This type of malware, called Petya, spreads via email. Here’s the process of infection:
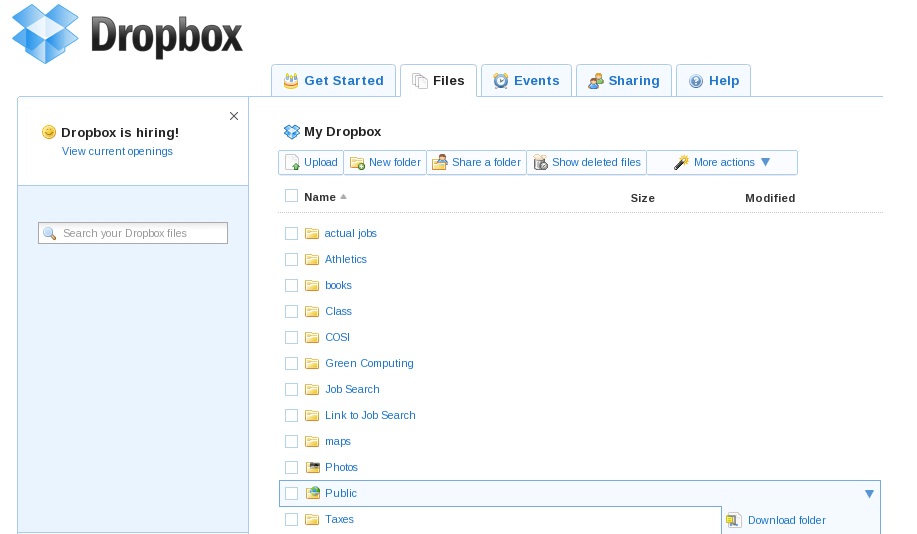
- HR managers of the organization receive an email from a potential candidate for a job, which includes a link to their resume and a photograph, both stored in Dropbox.
- When you click on the link, the user begins to download a self-extracting file that contains a Trojan.
- The malware gets into the antivirus program to help pave the way for its partner-in-crime, the ransomware, which later blocks the entire operating system.
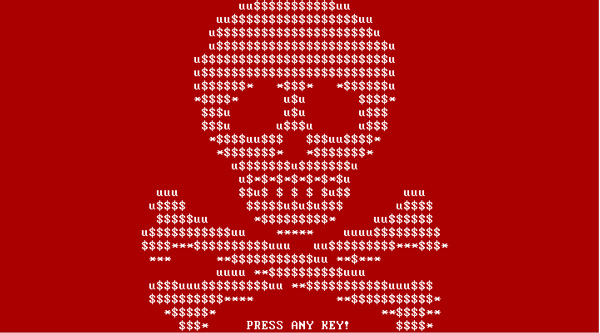
- Windows’ “blue screen of death” stamps the screen. Dun Dun Dun. If you try to restart the computer, you will see a skull on a red background with a message from the hacker. (Safe mode is pointless at this point because the malware disables it.)
The only way to regain control of your device and sensitive information is to pay a ransom. Currently, the approximate cost to release a system and files is around 0.99 bitcoins which exchanges to approximately €431,379 (bitcoins: the first digital currency. Although it has been said that this form of payment could be used for “legitimate” reasons, it’s more commonly used on the deep web as a form of payment for theft and the black market.)
It’s easy to be a victim in this scenario when there’s always someone looking to prey upon the desperate. In the summer of 2015, a group of security experts identified a number of emails sent to companies with resumes, and in this case, in a ZIP compressed file containing a malicious code.
Despite the uncertainty and fear that comes with an attack of this type, don’t give into the pressure! Paying the ransom does not guarantee that they are to unlock the infected computer (it might even motivate the perp to ask for an even larger sum instead.)
Infected, now what?
- The solution for someone affected would be to consult a computer or security expert (like those that are part of our technical team) to guide you in the process of eliminating the ransomware from your system and browser, and reconfiguring your computer.
- The absolute best way to prevent this kind of malware hijacking your system is by taking precautions, because generally, the users themselves are the ones opening (unknowingly) the doors to infection.
- Be sure to install all security patches and system updates, in order to keep the browser and antivirus updated. Regularly back-up your files.
- Try not to download documents or access links from unknown sources, and if you do, check their format.
- Lastly, keep updated with the new attacks and threats detected by security experts; this way you’ll know exactly what you should pay attention to.
As they say, prevention is always better than the cure.
The post Linked Out: how job-search platforms are being used for ransomware appeared first on Panda Security Mediacenter.
Source: Panda