Ransomware — malicious software that encrypts the victim’s files and holds them hostage unless and until the victim pays a ransom in Bitcoin — has emerged as a potent and increasingly common threat online. But many Internet users are unaware that ransomware also can just as easily seize control over files stored on cloud services.
 Toni Casala found this out the hard way. Casala’s firm — Children in Film — works as an advocate for young actors and their families. The company’s entire operations run off of application hosting services at a managed cloud solutions firm in California, from QuickBooks to Microsoft Office and Outlook. Employees use Citrix to connect to the cloud, and the hosting firm’s application maps the cloud drive as a local disk on the user’s hard drive.
Toni Casala found this out the hard way. Casala’s firm — Children in Film — works as an advocate for young actors and their families. The company’s entire operations run off of application hosting services at a managed cloud solutions firm in California, from QuickBooks to Microsoft Office and Outlook. Employees use Citrix to connect to the cloud, and the hosting firm’s application maps the cloud drive as a local disk on the user’s hard drive.
“We were loving that situation,” Casala said. “We can keep the computers here at work empty, and the service is very inexpensive when you compare it the cost of having more IT people on staff. Also, when we need support, they are very responsive. We don’t get farmed out to some call center in India.”
They were loving it, that is, until just before New Year’s Eve, when an employee opened an email attachment that appeared to be an invoice. Thirty minutes later, nobody in Casala’s firm could access any of the company’s 4,000+ files stored on the cloud drive.
“Someone in my office was logged into Outlook and opened up invoice attachment and BAM!, within 30 minutes, every single file on our Q drive had ‘vvv’ added as file extensions,” she said. Every single folder -had a file that said “help.decrypt,” essentially the attacker’s’ instructions for how to pay the ransom.
The cloud provider that Casala’s company is using was keeping daily backups, but she said it still took them almost a week to fully restore all of the files that were held hostage. She said the hosting service told her that the malware also disrupted operations for other customers on the same server.
Casala said her company got lucky on several fronts. For starters, the infection happened right before her firm closed down operations for the New Year’s break, so the outage was less of a disruption than it might normally have been.
More importantly, the malware that scrambled their files — a strain of ransomware called TeslaCrypt, contained a coding weakness that has allowed security and antivirus firms to help victims decrypt the files without paying the ransom. Users over at the computer help forum BleepingComputer have created TeslaDecoder, which allows victims to decrypt files locked by TeslaCrypt.
Casala said the hosting firm had antivirus installed on the server, but that the ransomware slipped past those defenses. That’s because the crooks who are distributing ransomware engineer the malware to evade detection by antivirus software. For more on how cybercriminals achieve that, see Antivirus is Dead: Long Live Antivirus.
The best defense against ransomware is a good set of data backups that are made each day — preferably to a device that is not always connected to the network. Unfortunately, this is often easier said than done, especially for small businesses. For many ransomware victims who do not have backups to rely upon, the choice of whether to pay comes down to the question of how badly the victim needs access to the ransomed files, and whether the files lost are worth more than the ransom demand (which is usually only a few hundred dollars in Bitcoin).
Many readers may have a hard time believing that ransomware peddlers will actually return the encrypted files to their original state if the ransom is paid. But cyber criminals who run these schemes have a vested interest in making sure the transaction is a relatively seamless one: They understand that if word gets out that victims aren’t getting their files back after paying, fewer victims will pay. What’s more, the amount demanded in ransom is about hitting that sweet spot: Thieves know that if they demand too much from each victim, they’ll have fewer victims who end up paying.
That said, ransomware is computer code, and even malware coders make mistakes. Every so often, crooks will release a new version of ransomware that contains critical programming errors, effectively rendering the victim’s files unrecoverable even if they do pay the ransom.
One big reason that ransomware scams are becoming more prevalent has to do with the proliferation of plug-and-play tools and services that make it simple to start your own cybercrime syndicate. Earlier this month, security firm Emsisoft published a fascinating look at a crimeware-as-a-service product being marketed in the underground called Ransom32, which allows anyone to start their own ransomware campaign just by providing a Bitcoin address to which victims will be asked to send the funds.
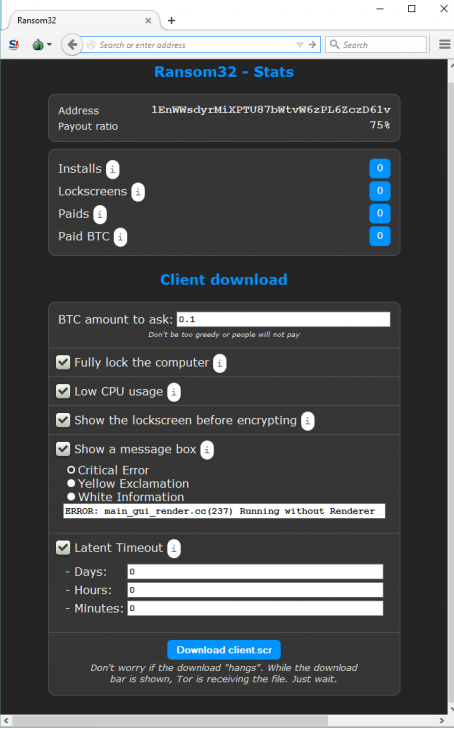
The crimeware as a service ransomware package, Ransome32. Image: Emsisoft.
“After you type in your Bitcoin address, you will get access to the rudimentary administration panel,” the company explained. “In the admin panel, you can get various statistics, like for example how many people already paid or how many systems were infected. You can also configure your “client”, which is their term for the actual malware. It is possible to change the amount of Bitcoins the malware will ask for, as well as configure parameters like fake message boxes the malware is supposed to show during install.”
According to Emsisoft, the Ransom32 crimeware service also includes a feature that offers to decrypt a single file to demonstrate that the malware author has the capability to reverse the encryption.
It seems to me that ransomware attacks have a great deal of room for growth. I would expect criminals who have the skills to construct and manage their own ransomware campaigns eventually to begin doing a better job targeting victims — that is, taking the extra time to get a better idea of how much the ransomed files are worth, and then adjusting the ransom demand accordingly.
If you or your company is hit with ransomware, resist the temptation to pay up, which just perpetuates these scams. Take a deep breath, head on over to BleepingComputer’s ransomware removal section, which includes resources that may allow you to recover files without rewarding the crooks.
Source: Krebs