Shadow Copies: Taking advantage of ransomware tricks
There are not many ways to recover our kidnapped files from a ransomware attack without paying the ransom. If we are lucky (really lucky!) there might be some free tool to recover them, another option is to restore your files from your backup. However not everyone has a backup in place, although Windows has a very useful feature known as Shadow Copy, which in short is a backup of our files. Cybercriminals learned this ages ago, which means that a few months after these attacks became popular, one of the first things they do when they infect our computer is to delete the Shadow Copy of our files before encrypting our information.
There are a number of technologies that can be applied to stop ransomware attacks; some of them are almost useless, such as signatures or heuristics (that’s the first thing malware guys check before releasing their new creations), some others can be a bit more successful sometimes, but even combining all of them together doesn’t guarantee that you will protect against all attacks.
More than 2 years ago (time flies!) we applied a simple but effective approach: if some process tries to delete the shadow copies it will be likely (not always) malware, with high chances of ransomware. Adding all the other information we have on top of it allows us to decide when it is a new malware. Nowadays most ransomware families do delete Shadow Copies; they could stop doing it, but then people wouldn’t pay the ransom as they could recover their files for free. I have taken a look at how many infections we do stop thanks to this. The logical deduction is that it will be a figure that has to be growing exponentially, as there are more ransomware attacks than ever and all of them use this trick. Well, this is what we have blocked in the last 12 months using this approach: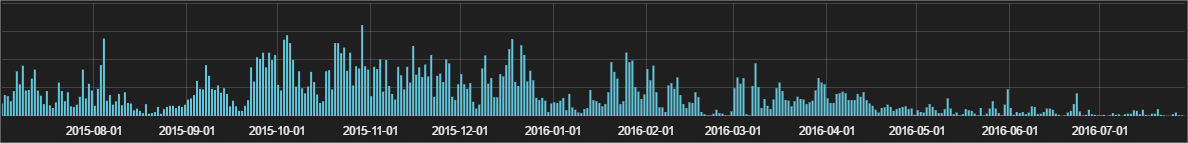
Yes, exactly the opposite of what most of us were thinking. How is this possible? Well, there is an easy explanation to this: we use this one as a “last resort”, when each and every other security layer has failed, this one will be triggered and will block the attack. In fact we use this internally to identify those attacks who have got through so we can analyze them in detail and improve the previous security layers. We also use this to measure how well / bad are we stopping ransomware, the lower the figure the better our previous technologies are working. And as you can see our performance is only getting better.
The post Tales from Ransomwhere: Shadow Copies appeared first on Panda Security Mediacenter.
Source: Panda

